IT services alone are not enough. Get the security you need.
Our next-generation Secure Managed Services offering is powered by a data platform in order to provide data-driven IT answers and embedded security that focuses on people and access.
The problem
Your organization’s data is valuable.
The ever-changing threat landscape means that today, more than ever, bad actors are working to steal and encrypt your data in ways that you may not be able to even see yet.
We've all seen the headlines...



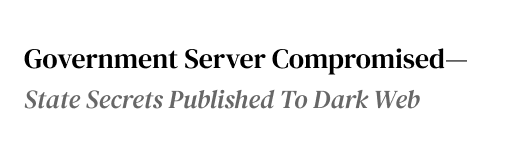
Growing cybercrime threatens every business today.

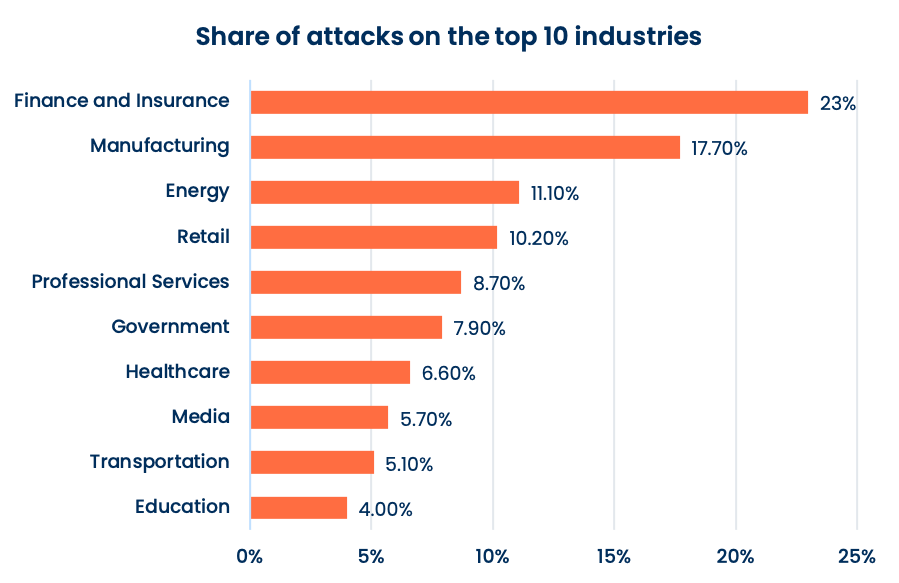
Phishing and spear phishing

Ransomware attacks

Zero-day attacks and known vulnerability exploits

Data breaches of personal and company-sensitive data

Brute-force attacks

Attacks against cloud platforms
The problem
Bad actors are attacking with increasing sophistication.
Because of these factors, your security infrastructure in place today may still have gaps.
Why Aunalytics Secure Managed Services includes embedded security
We can’t protect what we don’t manage. We can’t manage what we don’t account for through scanning, vulnerability management, monitoring, and log collection.
The Aunalytics Secure Managed Services Solution
Let us focus on managed services so you can focus on your business.
Peace of mind
Know that your environment is monitored and managed 24/7
Risk management
Eliminate the risk of your valuable infrastructure going down or being unavailable
Defined spend
Reduce and control your costs associated with resources required to monitor and manage critical infrastructure
Eliminate technical worries
Aunalytics manages all of the hardware and software for you and works proactively to address any errors or issues
How we work
Traditional managed services and security is no longer an efficient or risk mitigating approach. Instead, we use the Zero Trust Approach: Perimeter—the most up-to-date approach to ensure your data is protected, no matter its location.
Old World
One central working location, with security around the perimeter of one location
New World
Multiple, separate working locations, with identity and data focused secure access with full visibility

Aunalytics Service Desk
The Aunalytics Service Desk is comprised of knowledgeable technicians and engineers working in tandem to tackle technical issues—both simple and complex—that impact our clients. We encourage our Service Desk team members to advance their skills through continuing education and achievement of technical certifications. When you contact our Service Desk, you will be assisted by hardworking, dedicated professionals who go above and beyond to provide technical answers and solutions for our clients.
Aunalytics Network Operations Center (NOC)
The Aunalytics NOC is constantly monitoring our customer’s technology assets as well as our own platforms for any issues. The dedicated NOC team is made up of engineers with a broad set of expertise so they can respond to any alert at any time. Our advanced monitoring tool ecosystem allows us to not only respond to equipment that is reporting down in a timely manner, but also to proactively detect system issues and repair them ahead of downtime.

Let us manage your tech environment
We spend time on your IT support so you can focus on your business.
Components
Aunalytics Secure Managed Services isn’t just a bunch of tools. We provide managed components that offer stability and security to your environments.
Trusted Advisors
Mitigate the risk of your valuable infrastructure going down or being unavailable.
Side-by-Side Approach
We act as trusted advisors for security, transferring cybersecurity risk management to our expertise. Package includes award winning products with experienced support staff that provide excellent customer service.


Critical IT paired with proactive security
We provide critical IT and security components, expertise, and operations for your business.
24/7/365 Remote Monitoring & Management
Aunalytics manages hardware and software for you and works proactively to address any issues all day, every day. Our remote monitoring agent includes client-based interactive support, performance management, alerting, asset management and reporting.
Allows you to:
- Mitigate the risk of your valuable infrastructure going down or being unavailable
- Achieve peace of mind that your systems are continuously monitored by our experts
- Solve issues with our interactive support
- Treat the service as an extension of your own IT team
- Understand your systems with expert guidance
- Achieve confidence in stability
- Achieve better performance and asset management results
Synchronized Network Security Platform
Protect networks and end points from advanced threats with next-generation anti-virus protection and management. We use award-winning Sophos Intercept X for ransomware protection, deep learning malware detection, exploit prevention, EDR, and more in a single solution.
Allows you to:
- Mitigate the risk of your valuable data being breached by a cyberattack
- Stop threats faster with powerful remote response capabilities
- Automatically prioritize potential threats and responses
- Quickly know which machines may be impacted
- Recognize known and unknown malware threats faster with AI and deep learning powered threat detection
- Halt ransomware and boot record attacks with automatic file protection, recovery and behavioral analysis
- Deny attackers by blocking the exploits and techniques used to distribute malware, steal credentials, and escape detection
- Prevent persistence on machines, credential theft and malicious traffic with active adversary mitigation
- Treat the service as an extension of your own IT team
- Achieve confidence in security
Internet Protection
Guard against Internet breaches with our Sophos Central and Cisco Umbrella combined solution providing website protection, DNS filtering and roaming DNS protection.
Allows you to:
- Connect to the Internet with confidence
- Achieve security protection on and off network
- Keep consistent security policies across remote locations
- Block unwanted traffic
- Stop threats before they reach your network
- Enforce acceptable use policies
- Expose shadow IT, detect and report cloud applications in use across your organization
- Achieve peace of mind that experts are monitoring the Internet for malicious domains, IPs and URLs on your behalf
- Enable faster incident investigation and response based upon real-time threat context data for malware, phishing, botnets, trojans and other threats
Workstation & Server Patching
Ensure your servers and workstations are always protected through operating system security patching, including feature releases.
Allows you to:
- Ensure your servers and workstations have protection from the latest security threats
- Achieve peace of mind that experts are keeping your servers and devices updated for you
Office 365 Management & Security
Manage and protect your O365 instance with Microsoft Defender Advanced Threat Protection.
Allows you to:
- Mitigate against credential phishing
- Rest easy that user behavior is automatically monitored to detect atypical behavior of an attacker from valid user activity
- Minimize common attacks targeting Microsoft cloud based products
Email Filtering & Security
Protect your team’s email inboxes with Microsoft Defender Advanced Threat Protection.
Allows you to:
- Mitigate business email compromise cyberattacks
- Protect your team’s email inboxes
- Reduce opportunities for your team members to innocently click on harmful links or open harmful attachments
Multi-Factor Authentication
Restrict access with Duo or Okta-based multi-factor authentication solutions.
Allows you to:
- Restrict system access to only authorized users
- Achieve peace of mind with a second layer of user authentication to protect against unauthorized access by an attacker
Data & Device Encryption Management
Encrypt data and restrict access with Sophos Central Encryption.
Allows you to:
- Protect your data
- Restrict data access to only authorized viewers
- Restrict device access to only authorized users
- Meet compliance safe data handling standards with a remote workforce
- Verify device encryption status to demonstrate compliance
Security Awareness Training
Train your team to be more security-aware. As attacks are more people-focused than ever, we help you drive effective security training and testing campaigns.
Allows you to:
- Empower your team with knowledge of attacks
- Prepare your team to recognize attacks
- Prevent team members from innocently falling victim to an attack, compromising company data, reputation or operations
- Train your team to report suspicious activity
- Assess your team’s security acumen with our security testing campaigns
Managed IT Service Uplifts
Line of Business Application Support
Aunalytics offers support and vendor liaison services for business applications, such as accounting software or ERP systems.
Hardware-as-a-Service (HaaS)
Aunalytics offers optional HaaS for infrastructure equipment for our Managed IT Services clients.
Identity and Access Management
Aunalytics offers Okta-based Adaptive MFA, Single Sign-on (SSO), and Lifecycle Management options.
“We have made the paradigm shift from trying to operationalize a collection of IT and security tools to a holistic view of stability and security that adapts as ever-changing threats evolve.”
– Kerry Vickers, Chief Information Security Officer, Aunalytics
Questions around Aunalytics Secure Managed Services? Let's get them answered.
Looking for more information? Let us know and an account manager will be in touch.
