Carolinas' LAUNCH 2025
Carolinas' LAUNCH 2025
Embassy Suites by Hilton Charlotte Concord, Concord, NC
Aunalytics to attend Carolinas Credit Union LAUNCH 2025
Aunalytics is thrilled to be an exhibitor at the Carolinas Credit Union LAUNCH 2025 in Concord, NC on February 12-13, 2025. Aunalytics will be at booth #1 to educate credit union stakeholders on how our technology solutions can make their jobs easier and more effective.
The Sightglass Productivity Platform enables credit unions to use AI to increase deposits and more effectively identify and deliver new services and solutions—allowing them to compete with large national banks. Aunalytics also partners with credit unions to deliver cloud, backup, and managed IT solutions that are robust and secure—streamlining the implementation process and providing solutions as-a-service.

Cybersecurity Controls Checklist
Cybersecurity Controls Checklist
Cybersecurity standards are constantly evolving as cyberattacks get increasingly complex. The following checklist from the Center for Internet Security (CIS) will allow your organization to evaluate whether the correct controls and safeguards are in place to meet global cybersecurity standards.
Related Content
Nothing found.
Paulding-Putnam Electric Cooperative Transitions IT Infrastructure to the Cloud to Provide a Superior Customer Experience - PDF
Paulding-Putnam Electric Cooperative Transitions IT Infrastructure to the Cloud to Provide a Superior Customer Experience
Related Content
Nothing found.
Western Michigan University IT Forum Conference 2024
IT Forum Conference
Schneider Hall at Western Michigan University, Kalamazoo, MI
David Cieslak, Chief Data Scientist at Aunalytics, to speak at 2024 WMU IT Forum Conference
Aunalytics is excited to participate in the 2024 Western Michigan University IT Forum Conference in Kalamazoo, MI. David Cieslak, PhD, Chief Data Scientist at Aunalytics, will be giving a talk entitled, “Returning to the Mission of AI: Solving for Workload Imbalance“. Representatives from Aunalytics will also be on hand to discuss cybersecurity, IT, and AI topics with attendees.

Understanding the Hackers' Playbook: How to Prevent Cyberattacks and Adopt Good Practices
As increasingly sophisticated cyber threats pose risks to companies of all sizes, understanding how to prevent cyberattacks and implement good safety practices is important for any organization. This blog post discusses the common threats that companies face, effective cybersecurity strategies, and best practices for maintaining robust defenses. We’ll also explore how to foster a culture of security awareness and prepare for rapid recovery after an incident.

Understanding Common Cyberattacks
To effectively combat cyberthreats and develop smart strategies, organizations must be able to recognize common threats. One increasingly common type of attack is an opportunistic attack—attacks based on available opportunities rather than specific targets. One of the most prevalent opportunistic attacks involves exploiting known vulnerabilities—weaknesses in software or systems that, if left unpatched, can be leveraged by hackers to gain unauthorized access. For example, the Experian data breach demonstrated the dangers of neglecting known vulnerabilities. Despite being aware of the issue for weeks, Experian’s IT team failed to act, resulting in a massive compromise of personal data. This incident highlights the importance of timely patch management and proactive security measures.
Another critical threat is the compromise of business email accounts, often leading to the exploitation of platforms like Office 365. Common risk factors include the lack of Multi-Factor Authentication (MFA) and poor security practices. While MFA can significantly reduce the risk of unauthorized access, many organizations still avoid implementing it, often due to perceived inconvenience. However, the benefits of MFA far outweigh the hassle, making it a fundamental component of a strong security posture.
While technologies such as MFA are extremely effective at preventing cyberattacks, it doesn’t prevent all breaches. Phishing, though a simple, well-known concept, remains one of the most effective and damaging methods of cyberattack. Phishing emails trick recipients into divulging sensitive information or clicking on malicious links. It is all too easy for a single employee to have a brief lapse in judgement that puts an organization at risk. To combat this, phishing-resistant MFA and ongoing employee training are essential.
Key Components of an Effective Cybersecurity Strategy
To build a robust cybersecurity strategy, it’s essential to implement layered defenses and understand the key principles of security management. Phishing-resistant MFA adds an extra layer of security by requiring multiple forms of verification before granting access. This makes it significantly harder for attackers to gain unauthorized access through stolen credentials.
Additionally, understanding the shared responsibility model is crucial. Organizations must know their responsibilities and choose technology providers that align with their security needs. This includes ensuring that all security measures are covered and that responsibilities are clearly defined.
Employing established security frameworks, such as the NIST Cybersecurity Framework (CSF), can also provide a structured approach to managing and mitigating cybersecurity risks. These frameworks offer guidelines on identifying, protecting, detecting, responding to, and recovering from cybersecurity incidents.
Keeping Cybersecurity Policies Up-to-Date
Security threats are constantly evolving as hackers develop increasingly complex methods and uncover new vulnerabilities. To maintain a strong cybersecurity posture, organizations must continuously adapt their strategies—regularly reviewing and updating policies is essential. This includes conducting periodic assessments and audits to ensure that policies remain effective and relevant. It is also beneficial to regularly test and refine response plans by conducting tabletop exercises to simulate cybersecurity incidents. These exercises help organizations prepare for real-world scenarios and improve their incident response strategies.
As tactics evolve and new vulnerabilities are uncovered, organizations must stay informed of the latest security news and intelligence. This can include gathering threat intelligence from partners and industry sources, and staying informed through news articles, social media, and threat intelligence feeds. Additionally, engaging in a crowdsourced approach to security allows organizations to tap into a broader pool of knowledge and expertise. Participating in cybersecurity forums and collaborating with external security experts can take this knowledge a step further and helps organizations learn how to proactively address potential risks.
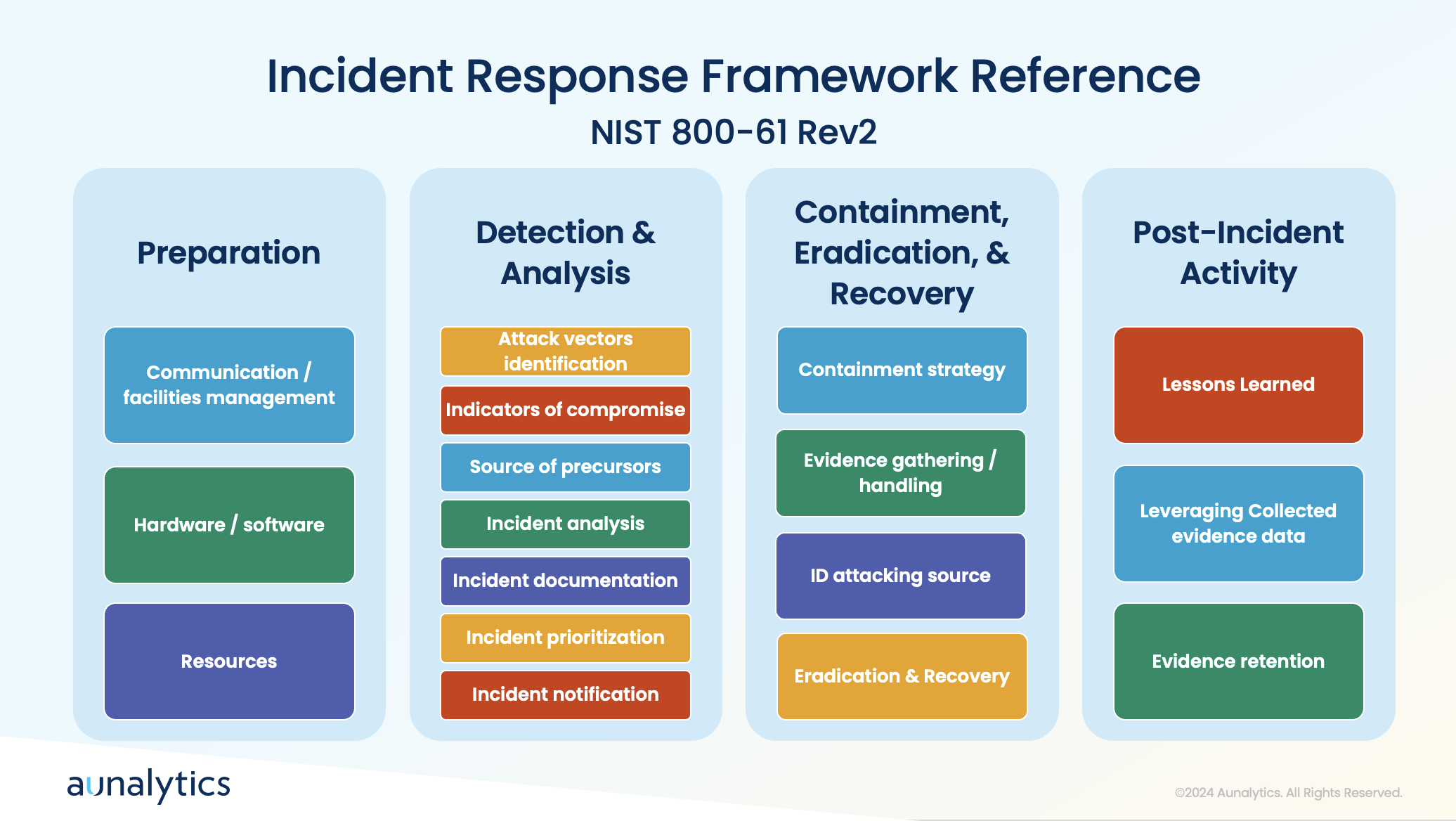
Best Practices for Incident Response
While putting safeguards in place to prevent cyberattacks from occurring is imperative, it is also equally important to prepare your organization to respond appropriately when an incident does occur. During a cyberattack, it’s crucial to have tools in place to detect anomalies and communicate effectively. Quick actions include containing the incident by taking affected systems offline, blocking access to malicious platforms, and assessing the scope of the breach.
A clear communication plan and understanding of the attack’s attribution are essential for effective recovery. Preparation involves establishing processes for detection, analysis, containment, eradication, and recovery, followed by post-incident activities to improve future responses.
Employee Training and Awareness

To ensure that all areas of a company take an active role to prevent cyberattacks, it’s crucial to foster a strong security culture. Unfortunately, employees often make mistakes that lead to breaches, such as falling for phishing schemes or responding to solicitation calls. Educating staff about the tactics used by attackers, such as impersonation and social engineering, can help prevent these errors.
Therefore, it is crucial to ensure that all employees have access to cybersecurity training—this training covers the basics of recognizing bad actors and avoiding common traps.
Tailoring training to specific roles and conducting phishing email simulations can enhance employees’ ability to identify and respond to threats. Creating a culture of cybersecurity awareness involves emphasizing the importance of security to employees and their families. This helps instill a sense of personal responsibility for maintaining security practices.
For IT and cybersecurity professionals, it is greatly beneficial to focus on developing a strong understanding of network engineering, including routing, switching, and firewall management. Additionally, the ability to visualize and comprehend data flows and security information is crucial for effective security management. IT teams must avoid cutting corners and ensure robust security measures are in place. They play a critical role in enforcing security policies and preventing breaches, making their diligence essential.
Conclusion
Understanding the tactics used by attackers and implementing robust preventive measures is key to safeguarding your organization. By adopting best practices such as phishing-resistant MFA, regularly updating policies, leveraging threat intelligence, and training employees effectively, companies can significantly reduce their risk of cyberattacks. Additionally, having a well-defined incident response plan and fostering a culture of security awareness ensures preparedness for any potential breaches. By following these guidelines, organizations can better protect their data and maintain a strong defense against cyber threats.

Partnering with Aunalytics ensures your data privacy and security through a comprehensive approach that includes advanced risk assessments, phishing-resistant Multi-Factor Authentication (MFA), and continuous updates to align with industry standards like the NIST Cybersecurity Framework. Our expert team provides 24/7 monitoring and rapid threat response, leveraging cutting-edge technology and threat intelligence to preemptively address risks. With Aunalytics, you benefit from top-tier protective measures and a commitment to adapting strategies to emerging threats, ensuring your data remains secure and confidential.
GoWest MAXX Convention 2024
GoWest MAXX Convention 2024
Gaylord Rockies Resort & Convention Center, Aurora, CO
Aunalytics to attend the 2024 GoWest MAXX Convention
Aunalytics is thrilled to be an exhibitor at the 2024 GoWest MAXX Convention in Aurora, CO on October 13-16, 2024. Aunalytics will be at booth #193 demonstrating our member intelligence solution which enables credit unions to use AI to increase deposits and more effectively identify and deliver new services and solutions—allowing them to compete with large national banks.

2024 Jack Henry Connect
2024 Jack Henry Connect
Phoenix Convention Center, Phoenix, AZ
Aunalytics to attend 2024 Jack Henry Connect
Aunalytics is excited to attend 2024 Jack Henry Connect. Representatives from Aunalytics will be demonstrating our customer intelligence solution at booth #830. Aunalytics enables financial institutions to increase deposits and more effectively identify and deliver new services and solutions for their customers and members so they can better compete with large national banks.

2024 BankTech Conference
2024 BankTech Conference
DoubleTree by Hilton Hotel Chicago - Oak Brook, Oak Brook, IL
Aunalytics to be featured at the Innovators' Showcase at the 2024 BankTech Conference
Aunalytics is excited to attend and exhibit at the 2024 BankTech Conference, presented by a partnership of Illinois, Indiana, Michigan, and Ohio state banking associations in Oak Brook, IL. Kyle Davis, VP, Managed Analytics from Aunalytics will be demonstrating how our customer intelligence solution enables banks to increase deposits and more effectively identify and deliver new services and solutions for their customers so they can better compete with large national banks.

2024 Indiana Credit Union League Annual Meeting & Convention
2024 Indiana Credit Union League Annual Meeting & Convention
JW Marriott Indianapolis, Indianapolis, IN
Aunalytics to attend the 2024 Indiana Credit Union League Annual Meeting & Convention
Aunalytics is thrilled to be an exhibitor at the 2024 Indiana Credit Union League Annual Meeting & Convention in Indianapolis, IN on October 2 – 4, 2024. Aunalytics will be at booth #20 demonstrating our member intelligence solution which enables credit unions to use AI to increase deposits and more effectively identify and deliver new services and solutions—allowing them to compete with large national banks.

Digital Transformation in Community Banking Webinar
Digital Transformation in Community Banking
With the help of AI technologies, community banks have successfully been able to strengthen relationships, reduce churn, increase deposits, and improve ROI enterprise-wide by utilizing the data they already have at their fingertips—and your organization can, too. However, successful digital transformation can be a major challenge for midsized and community-based banks. Adopting new technologies, shifting operational mindsets, and hiring the talent necessary to build and execute upon AI solutions is a major endeavor. Many banks do not even know where to begin. In this presentation, discuss the steps and considerations for aggregating data across your bank to create a 360-degree view of your customers, why that is important, and ways other community banks have found success through analytics initiatives.
Related Content
Nothing found.