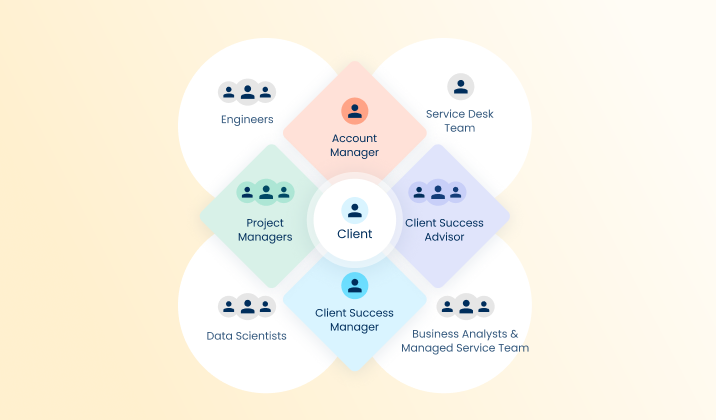
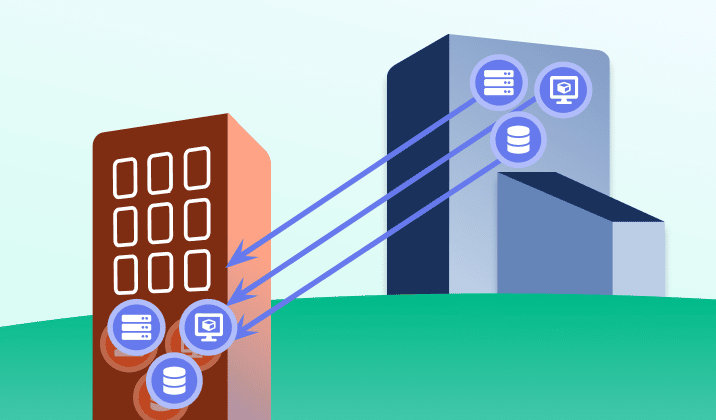
The Cost of Skimping on Security in 2022
From 2020 to 2021, the number of ransomware attacks on organizations increased by 78% and more than 10% of those attacks resulted in ransoms of $1 million or higher. According to the Sophos State of Ransomware 2022 report, ransomware attacks take an average of one month to fully recover from and frequently result in downtime and loss of revenue, the impact of which leads to an average recovery cost of $1.4 million. That’s about 640 vacations to Disney World. The cost of skimping on security is great.
While you could take your entire team to Disney World for a week, possibly even a few times over, a better idea might be to invest in preventing a security breach in the first place. Be it ransomware, a phishing attack, or an insider threat, proactive threat and risk prevention takes dedicated time, well-trained people, and cutting-edge technology, so it is no surprise that it can be confusing and costly. As we’ve already seen, it can be even more costly to ignore those risks.
Keeping Up with Technology
It took 2 million years for humans to progress from the first tools to discovering fire, yet it only took 130 years to go from the telegraph to the internet and another 33 years to get to the iPhone. Technology now changes at a blistering pace and, alongside that thrives the unfortunately fruitful business of cybercrime. One of the most critical factors in combating this is having, understanding, and fully utilizing the latest technology. Based on Gartner’s 2022 report of Top Strategic Trends, some of the newest technologies that will impact the cybersecurity field include:
- Cybersecurity Mesh: A scalable, integrated architecture that enables security tools to work cooperatively throughout an environment
- Autonomic Systems: Self-managing systems that take in information from the network to modify algorithms without manual updates, allowing for rapid changes and scalability
Source: Gartner
Partnering with the Experts

Whether you are intimately familiar with the concepts presented here or they sound like something from the USS Enterprise, partnering with experts is what will give you an advantage over bad actors and cyber criminals. Admittedly, most organizations struggle to keep up with regular patching, let alone investing the time and resources into implementing these types of technology. While cybersecurity and understanding cyber risk are likely not your area of expertise, working with a trusted partner can ensure that your online business and IT landscape are as secure as technology and expertise allow. Having security that stands up to the worst of ransomware, hackers, and more is a must.
The criminals don’t take a break, so your security monitoring can’t either, which is why it is critical to have both the technology to meet the needs of today’s risks as well as the people to understand, implement, and manage that technology to its fullest potential. Aunalytics has you covered. With expert toolsets and talent, your business can depend on us to have highly trained professionals and the newest technology and information to protect your business in the ongoing threat landscape.
How to Win Wallet Share While Cutting Costs in Financial Institution Operations
How to Win Wallet Share While Cutting Costs in Financial Institution Operations
In a recession economy, it is imperative to cut costs and employ efficient strategies to grow operating income. Here’s what banking institutions can do to make marketing and sales teams more efficient, and achieve better returns.

Fill out the form below to receive a link to the article.
Aunalytics is a data platform company. We deliver insights as a service to answer your most important IT and business questions.
How to Win Wallet Share While Cutting Costs in Financial Institution Operations
How to Win Wallet Share While Cutting Costs in Financial Institution Operations
In a recession economy, it is imperative to cut costs and employ efficient strategies to grow operating income. Here’s what banking institutions can do to make marketing and sales teams more efficient, and achieve better returns.
Bridging the Mid-Market Talent Gap for Digital Transformation
Bridging the Mid-Market Talent Gap for Digital Transformation
To achieve business value from data technology investments, mid-market companies need the right technical expertise and talent. Yet many mid-market firms push this onto their IT manager, assuming that since it is technology related, IT has it. This is a mistake because most IT departments do not have time for data analytics. They are busy full time keeping company systems stable and secure, and providing support to your team members. This by necessity results in IT deprioritizing data queries over crucial cybersecurity attack prevention. Business analysts and executives get frustrated waiting for data query results, and the data is stale or the business opportunity has passed by the time query results are in.

But even if your IT team had time for it, it still is a mistake to rely on traditional technology administrators for data analytics success. This is unless your IT department has expertise across a wide range of skill sets, from cloud architecture, database engineering, master data management, data quality, data profiling, and data cleansing. What’s more, your IT manager would need to have command over data integration, data ingestion, data preparation, data security, regulatory compliance, data science, and building pipelines of data ready for executive reporting from multiple cloud and on premises environments.
When you read this laundry list of needs, it becomes clear that most mid-market IT departments lack the specialized experts needed to derive business value from their data. Unlike larger enterprises that have the resources to hire skilled staff for these roles, the mid midsize organization requires another option that provides access to the right tools, resources, and support. One that integrates, enriches and is trained in utilizing AI, machine learning, and predictive analytics to achieve more useful results.

To read more, please fill out the form below:
Don’t Let Your Sensitive Data Go Unprotected
Every business has sensitive data that should not be shared with the world at large. Credit card information, personal details, company records—all of this data can be exposed or stolen and ransomed via a single bad actor.
Is Your Data Safe?
Everyone from banks and credit unions to government agencies and utility companies need one basic thing that can stop bad actors: good data security. With hackers and ransomware encroaching on your network, it’s more important than ever before that you have proactive data protection in place.
Good data security includes 24/7/365 monitoring of your network, constant threat and vulnerability scanning, a functioning Security Operations Center (SOC) and more. The problem? It’s hard to find talent to maintain a functional SOC, and when you do find talent your mid-market business may not be able to compete with offers from large enterprises.
While finding, paying, and retaining high quality talent is hard, partnering is not. A side-by-side approach with a knowledgeable partner allows you to actively react to the ever-changing digital landscape—not after your company’s security has been left behind and open for bad actors.
How Can You Protect Your Data?
Many security tools are made for experts—security engineers, network engineers, and others with specific technical expertise. Because the security landscape keeps changing, as bad actors evolve techniques and new threats are constantly emerging, security requires full time dedication to researching and staying up to date with threats, new prevention measures and remediation best practices. Most IT departments do not have time for the research and adaption that security requires. If you don’t have a team that can constantly update your security to provide your company with the best security possible, your security posture will begin to sag. A sagging posture isn’t good for any industry or company—and it needs to be fixed immediately.
By hiring a trusted partner, you can ensure that your sensitive data is secure. Having security that stands up to the worst of ransomware, hackers, and more is a must. An SOC takes care of things for you.
If your company doesn’t have an SOC, it is falling behind. Out of date security means injury to your network becomes more and more likely, and a security event can cause you to lose clients and prospects, large sums of money, and even tarnish your company’s reputation.
Partnering Up
You should already have an internal IT team. Aunalytics’ SOC isn’t meant to replace your IT team, but to supplement and support your team’s security initiatives. An SOC can stop threats before they enter your network and cause chaos, keeping your data out of the hands of bad actors everywhere.
When you need to protect your data, Aunalytics has you covered. With expert toolsets and talent, your business can depend on us to have highly trained experts and the newest technology and information to protect your business in the ongoing threat landscape.
Bridging the Mid-Market Talent Gap for Digital Transformation
Bridging the Mid-Market Talent Gap for Digital Transformation
To achieve business value from data technology investments, mid-market companies need the right technical expertise and talent. Yet many mid-market firms push this onto their IT manager, assuming that since it is technology related, IT has it. This is a mistake because most IT departments do not have time for data analytics. They are busy full time keeping company systems stable and secure, and providing support to your team members. This by necessity results in IT deprioritizing data queries over crucial cybersecurity attack prevention. Business analysts and executives get frustrated waiting for data query results, and the data is stale or the business opportunity has passed by the time query results are in.

But even if your IT team had time for it, it still is a mistake to rely on traditional technology administrators for data analytics success. This is unless your IT department has expertise across a wide range of skill sets, from cloud architecture, database engineering, master data management, data quality, data profiling, and data cleansing. What’s more, your IT manager would need to have command over data integration, data ingestion, data preparation, data security, regulatory compliance, data science, and building pipelines of data ready for executive reporting from multiple cloud and on premises environments.
When you read this laundry list of needs, it becomes clear that most mid-market IT departments lack the specialized experts needed to derive business value from their data. Unlike larger enterprises that have the resources to hire skilled staff for these roles, the midsize organization requires another option that provides access to the right tools, resources, and support. One that integrates, enriches and is trained in utilizing AI, machine learning, and predictive analytics to achieve more useful results.
Achieving Digital Transformation
Digital transformation has been defined by some as the integration of digital technology into all areas of a business, fundamentally changing how employees operate and deliver value to customers. Some of the challenges midsize businesses have with building an internal team to initiate this concept are employee pushback, lack of expertise to lead digitization initiatives, improper organizational structure, the absence of a digitization strategy and limited budget. As an alternative to building an internal operation, a more efficient way for mid-market businesses is to leverage the skillsets of experts by partnering with a consolidated group of experts, leveraging a side-by-side model that couples technology with talent. Look for solution providers that offer the following:

- Powerful cloud data centers paired with engineers skilled in architecting cloud-based applications and processes that better serve critical business requirements. These data centers are optimized for true multi-tenancy, built on seamlessly integrated hardware and software, offer business-driven configurability, world-class security and performant systems.
- Active Monitoring and Thoroughly Integrated Security. Monitoring and security should be pervasive across system infrastructure to defend against cyberattacks and provide remediation when required. Business customers will also expect full-time monitoring and on-demand help desk to address unexpected events. The data management platform underpinning applications should be monitored by experienced data engineers with success in building data warehouses, data lakes, and data pipes. They should also be able to integrate, cleanse, and transform data into decision-ready and analytics-ready business information.
- High ROI Business Insights that Drive Results. Data analytics investments need to provide real business value by giving actionable insights and finding opportunities within your data. With this in mind, data analytics should include access to data scientists and business analysts versed in your industry. These experts should be equipped to design AI-powered algorithms that answer the most pressing questions based on real-world business challenges.
Mid-Market Data Transformation for Enterprise-Class Results
Ensuring the right mix of hardware, software and resulting services are available to maximize the data center capabilities—and their ability to manage and protect data—is crucial to effective mid-market digital transformation. To compete and drive value, the cloud data center provider must deliver at all levels, with customizable business intelligence solutions powered by an effective data management platform that is secure and compliant. Successful mid-market digital transformation thus requires a shift of responsibilities for infrastructure procurement and maintenance to a third-party provider backed by experienced staff and best-in-class infrastructure.
When implementing a digital transformation project, your company gains from the many benefits this brings, such as a higher return on your IT investment, increased employee and customer experience, and greater business agility. This is further enhanced by leveraging experienced cloud engineers, data engineers, security experts, data scientists, and other highly skilled technical resources—achieving true business value from the investment. And by partnering with experts, your company’s time, resources, and innovation can be focused on its core competencies.
Learn More
Nothing found.
Cybersecurity Best Practices - PDF
Cybersecurity Best Practices
Tips to help you stay safe online
Related Content
Nothing found.
Best Practices for Securing Your Network from Ransomware - PDF
Best Practices for Securing Your Network from Ransomware
Elevate your protection against ransomware and other network attacks
Related Content
Nothing found.