How to Keep Your Business Thriving in a World of Risks - PDF
How to Keep Your Business Thriving in a World of Risks
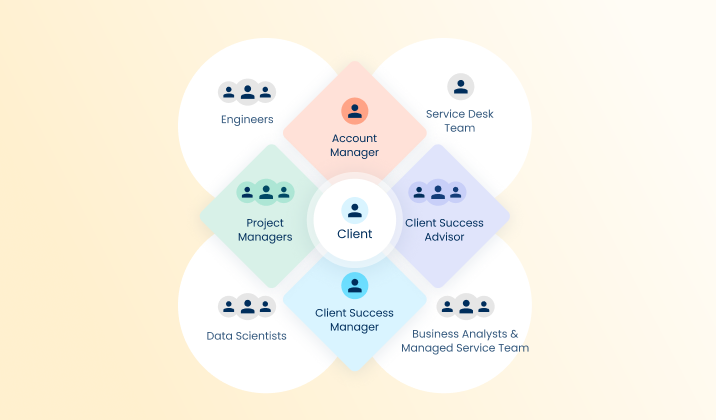
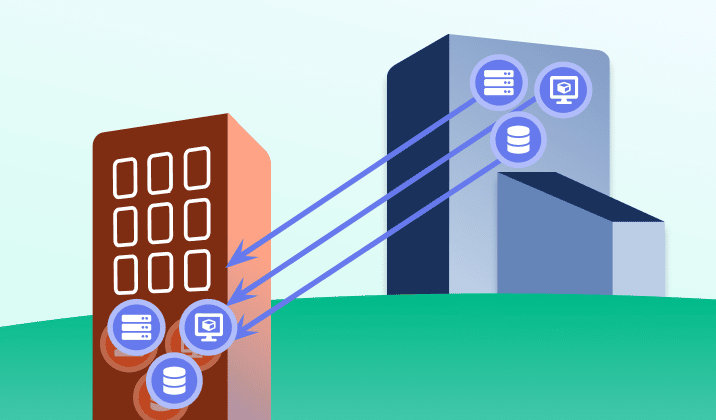
Managed security can protect your Business from cyber attacks
Related Content
Nothing found.
Cybersecurity for you - PDF
Cybersecurity for you
Enterprise-class IT protection for the small- to mid-size company
Related Content
Nothing found.
Why You Need Fresh Insights: Don’t Rely on Stale Data to Make Important Decisions
Why You Need Fresh Insights: Don’t Rely on Stale Data to Make Important Decisions
Too many mid-sized financial services institutions rely on reporting modules from their banking cores to try and understand business performance and make strategic decisions. However, there are problems with this approach.

Fill out the form below to receive a link to the article.
Aunalytics is a data platform company. We deliver insights as a service to answer your most important IT and business questions.
Why You Need Fresh Insights: Don’t Rely on Stale Data to Make Important Decisions - PDF
Why You Need Fresh Insights: Don’t Rely on Stale Data to Make Important Decisions
Too many mid-sized financial services institutions rely on reporting modules from their banking cores to try and understand business performance and make strategic decisions. However, there are problems with this approach.
Top 3 Actions for CIOs to Take Now in a Recession Economy
Top 3 Actions for CIOs to Take Now in a Recession Economy
The current economy poses a triple threat for business: persistent high inflation; scarce expensive talent; and global supply constraints. However, there are 3 actions CIOs should take to play offense to emerge from a recession on top.

Fill out the form below to receive a link to the article.
Aunalytics is a data platform company. We deliver insights as a service to answer your most important IT and business questions.
See Yourself in Cyber—How Individuals Can Reduce Security Risk
It seems like just yesterday our biggest security risk was a ‘long lost relative’ claiming we had millions of dollars waiting for us if only we would send them a little money up front. The world and technology have come a long way since then, and not always for the better. Now we are inundated with spam in the form of calls, texts, emails, and every other form of communication in existence—all alongside our actual conversations. Your grandma might message you on Facebook to ask for your help and it turns into requiring a trip to Walmart to buy $500 in Apple gift cards. Your CEO might text you with an urgent request when they’ve never texted you before. With this constant barrage of threats that continue to get more and more believable, is it even possible to be safe online? It most certainly is, but it requires vigilance and a keen, informed eye.

October is Cybersecurity Awareness Month in the US and this year’s theme is ‘See Yourself in Cyber’. Whether you’re the head of IT, a bank teller, a homemaker, or anything in between, you’re at risk of a cybersecurity attack. However, the industries experiencing the highest number of incidents are finance, healthcare, and public administration. As scammers, hackers, and generally ‘bad actors’ hone their craft, we also need to sharpen our detective skills. It’s an unfortunate truth, but we need to learn how to spot the red flags because it’s expected that, by 2025, there will be an average of 10 devices per person connected to the internet globally. All of which become a playground for cybercriminals if the devices aren’t well guarded by technology—and you.
Types of Threats
There are as many reasons bad actors attack as there are ways they do it. Understanding the most common methods will help you better avoid them in the wild. Here are some of the most widespread attacks you might see:
- Phishing: When a bad actor sends an email that appears to be from a reputable source or someone you are likely to trust in the hopes that you will open an infected attachment or follow a malicious link. This could allow them access to your system or persuade you to divulge personal information, such as passwords or credit card information.
- Spear Phishing: When a bad actor sends a phishing attack specifically targeting you. Typically, it will include information they’ve learned about you from social media or other online public forums.
- Smishing: This is phishing in the form of a text message.
- Vishing: This is phishing in the form of a phone call.
Spotting the Red Flags
For these types of threats, you’ll need to be able to identify something out of place to make you pause before taking any harmful actions. However, this is where vigilance is critical because these red flags are becoming increasingly more difficult to spot. Below you will find guidance on where you are most likely to spot a threat:
- Email is the most likely path a scammer will take. When identified separately, these signs may not seem concerning, but when combined, they are a sure sign of a phishing attack.
- Does the subject line or content of the email seem alarming or urgent?
- Is the email from someone unexpected or unknown?
- Is the ‘reply-to’ address different from the ‘from’ address?
- Did the email come in at an unusual time or day, such as in the middle of the night or on a weekend?
- Are there grammar or spelling mistakes?
- Does the wording seem unnatural?
- Are there unexpected or suspicious links or attachments?
- Are they offering you money or gift cards in exchange for an action?
- Is the email unexpected or out of place?
- Text messages may come in a different format, but they can still open you to the same security risks. Many of the red flags above still apply, but these are the most common examples in smishing.
- Is the sender claiming to be an executive at your company with an urgent need?
- If you know the sender, is the text from the number you have for them?
- Are you being asked personal information?
- Are you being asked to follow a link?
- Phone call scams commonly prey on the elderly and are more common outside of the workplace. Common signs to look for in vishing are:
- Is the call unexpected?
- Does the caller request access to your device to solve an issue?
- Does the caller threaten legal action or claim to be from a governmental body such as the IRS?
- Does the caller claim you have won money or a prize?
- Does the caller request payment in the form of gift cards or money orders?
Protecting Yourself
This feels like a lot of effort; what’s really the worst that can happen if you fall for one of these scams? If you click on a malicious link or download an infected attachment, you leave the door wide open for a hacker to access not only your device, but your entire network of devices and data. If they are able to access your personal information, they could potentially access your bank account, credit card information, or other private accounts. Shockingly, 88% of data breaches are caused by employee mistakes. Here are some steps you can take to ensure you aren’t part of that 88%:
- If an email comes from someone you work with, but you are noticing red flags, especially links or attachments, contact the person directly to verify they actually sent it.
- If there are links in the email, hover over them to ensure they match what is being displayed.
- Ensure links point to a trustworthy site. For example, you might receive an email from Microsoft asking you to reset your Outlook password, but when you hover over the link, it shows http://www.microsoftt.com/. Notice the misspelling in Microsoft.
- If you are unsure of a link, navigate to the website through your browser rather than clicking the link.
- If you receive an attachment that you didn’t expect, such as a financial statement when you don’t work in finance or a UPS shipping confirmation when you didn’t order anything, don’t open it until you can confirm its validity.
- Always remember, it is truly better safe than sorry when it comes to suspicious links or attachments.
This is just a small window into an ever-changing landscape of security threats. It might feel impossible to keep up as threats evolve, but there are ways to stay informed and vigilant for both you and your company. Through its Secure Managed Services Solution, Aunalytics provides the tools and talent you need to stay protect from outside threats, include a streamlined training platform to ensure you and your team can stay up-to-date with current threats and reduce security risk. When you are able to ‘See Yourself in Cyber’, you become critical in fighting against bad actors and the cyber threats they pose.
Aunalytics Security Operations Manager Rob Bradford to Deliver a Talk on the Cost of Skimping on Security in 2022 at BankTech Conference, Attended by Illinois, Indiana, Michigan, and Ohio Bankers
Leading Data Management and Analytics Company Will Feature Its Managed Services Solutions for Improving Operational Efficiencies and Reducing the Risks Associated with Cyber Attacks at Two Banking Events in October
South Bend, IN (September 29, 2022) - Aunalytics, a leading data management and analytics company delivering Insights-as-a-Service for mid-market businesses, announced today that Rob Bradford, Security Operations Manager for Aunalytics, will discuss The Cost of Skimping on Security in 2022 at the BankTech Conference on October 6. The company will also showcase its managed services, enterprise cloud, and data cleansing portfolio at the conference, in addition to the Indiana Bankers Association’s Security & Technology Conference, October 4-6.
Cyber-attacks are an increasing concern, especially for financial services firms which may experience up to 300 times more cyber attacks per year than other firms. Cyber criminals continue to double down efforts to breach financial data, compromise accounts, and profit from this industry with increasingly sophisticated attacks and campaigns. It is more critical than ever that banks work with the right IT services providers who have the security expertise, up-to-date knowledge of industry developments, and comprehensive tools to maintain a strong defense against cyber threats.
Aunalytics provides IT and security expertise to mid-market businesses in the areas of financial services, healthcare, manufacturing, professional services, and cities and local government. The company’s Secure Managed Services offering combines mission critical IT services leveraging zero-trust, end-to-end security to ensure data is protected regardless of a user’s location. Aunalytics provides managed components that offer stability and security, and its next-generation managed services offering is powered by a data platform that provides data-driven IT answers and embedded security that focuses on people and access.
The full suite of managed IT and integrated security services empowers businesses with a complete, all-encompassing approach that includes 24/7/365 monitoring and management, a synchronized network security platform, workstation and server patching, internet protection, email filtering and security, Office 365 management and security, multi-factor authentication, data and device encryption management, and security awareness training.
The company delivers advanced security for defending against modern threats through a team of engineers and analysts with expert skills and toolsets and, in regulated industries, Aunalytics provides the additional technology and controls required to manage risk. Its team of experts is dedicated to analyzing ever-changing rules and regulations and helping users to create processes and policies for data protection and meet compliance requirements within those industries that are regulated.
Aunalytics’ Enterprise Cloud offering is comprised of infrastructure solutions that provide a highly redundant and scalable platform for hosting servers, data, analytics and applications at any performance level. With the Aunalytics® Cloud Storage and Compute solution, users are assured the highest levels of security, accessibility, expertise, scalability, and savings. Aunalytics’ data centers, located in Northern Indiana and Southwest Michigan, meet the most rigorous compliance standards.
“Cyber security continues to be an important concern for banks and other financial institutions while cyber criminals are increasingly adept at executing attack campaigns,” said Steve Burdick, Vice President Sales, Cloud & Managed Services Aunalytics. “Working with a managed services provider who has the expertise to help with such things as vulnerability testing, proactive threat hunting, and ongoing monitoring helps reduce the burden on internal IT resources. Aunalytics’ full suite of managed IT and integrated security services solutions provides the tools and people resources mid-market banks need to adequately improve their security postures and maintain the highest levels of IT security to thwart cyber-attacks and reduce risk.”
Tweet this: .@Aunalytics Security Operations Manager Rob Bradford to Deliver a Talk on The Cost of Skimping on Security in 2022 at BankTech Conference, Attended by Illinois, Indiana, Michigan, and Ohio Bankers #Informationtechnology #Managedservices #Enterprisecloud #Datacleansing #Dataplatform #Dataintegration #Dataaccuracy #Digitaltransformation #ITsecurity #Securitytechnology #Banking #Midmarketbanks #Creditunions
About Aunalytics
Aunalytics is a leading data management and analytics company delivering Insights-as-a-Service for mid-sized businesses and enterprises. Selected for the prestigious Inc. 5000 list for two consecutive years as one of the nation’s fastest growing companies, Aunalytics offers managed IT services and managed analytics services, private cloud services, and a private cloud-native data platform for data management and analytics. The platform is built for universal data access, advanced analytics and AI – unifying distributed data silos into a single source of truth for highly accurate, actionable business information. Its DaybreakTM industry intelligent data mart combined with the power of the Aunalytics data platform provides industry-specific data models with built-in queries and AI for accurate mission-critical insights. To solve the talent gap that so many mid-sized businesses and enterprises located in secondary markets face, Aunalytics’ side-by-side digital transformation model provides the technical talent needed for data management and analytics success in addition to its innovative technologies and tools. To learn more contact us at +1 855-799-DATA or visit Aunalytics at https://www.aunalytics.com or on Twitter and LinkedIn.
PR Contact
Denise Nelson
The Ventana Group for Aunalytics
(925) 858-5198
dnelson@theventanagroup.com