Ransomware Attacks in Manufacturing Pose An Increasing Threat
Cyberattacks are a constant threat to organizations of all sizes. Manufacturing and production industries may have experienced fewer cyberattacks than other industries, but companies are still at risk from bad actors. To gain a better understanding of the current attack environment and track changes over time in ransomware trends, Aunalytics security partner Sophos commissioned an independent, vendor-agnostic survey of 5,600 IT professionals in mid-sized organizations across 31 countries. Out of all the respondents, 419 were from the manufacturing and production industry. This survey was conducted in January and early February of 2022. While it’s true cyber insurance has been playing a greater role in helping organizations improve their ability to recover from attacks, survey responses clearly indicate the rising threat ransomware poses to the manufacturing industry.
Cyberattacks Are Up From Previous Year
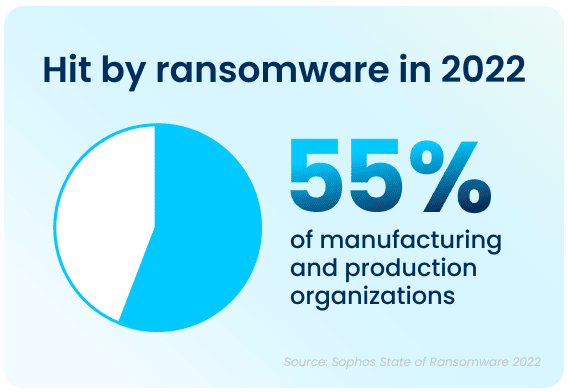
Ransomware attacks have increased significantly over the past year—55% of manufacturing and production organizations surveyed were hit by an attack in 2021, up 36% from 2020. Bad actors are now considerably more capable of attacking businesses and executing harmful tactics at scale. The Ransomware-as-a-Service model is one cause of this year’s increased attacks, as the required skill level for bad actors to hamper the day-to-day operations of an organization has gone down significantly.
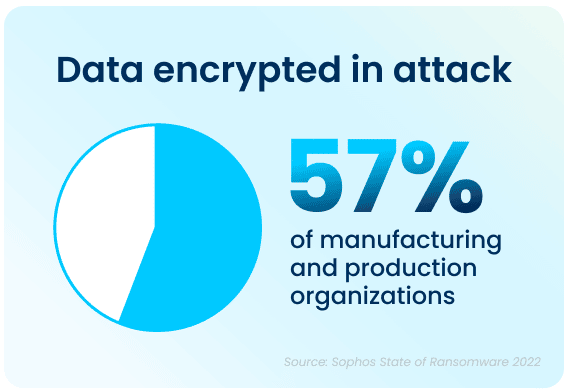
Apart from the rising prevalence of these attacks, the sheer complexity of each attack is also on an upwards trajectory. While the manufacturing and production industry reported the lowest rate of ransomware attacks, but, with over half of all respondents in all surveyed industries reporting that their company was been injured by bad actors, the reality is that every organization is at high risk of attack. In 2021, 57% of attacks in the manufacturing and production industry resulted in important data being encrypted. Additionally, 59% percent of organizations who experienced cyberattacks saw the complexity of the attacks increase, while 61% saw an increase in the overall volume of cyberattacks.
Data Recovery Rates Are Improving
While the increase in cyberattacks paints a bleak picture, there is a silver lining to this dark cloud. 96% of manufacturing and production organizations were able to get some of their encrypted data back. The top method used to restore data was backups, which were used by 58% of organizations whose data was encrypted in an attack. Unfortunately, despite the utilization of backups, a third of the effected organizations still had to pay a ransom to ensure that more their data was restored.
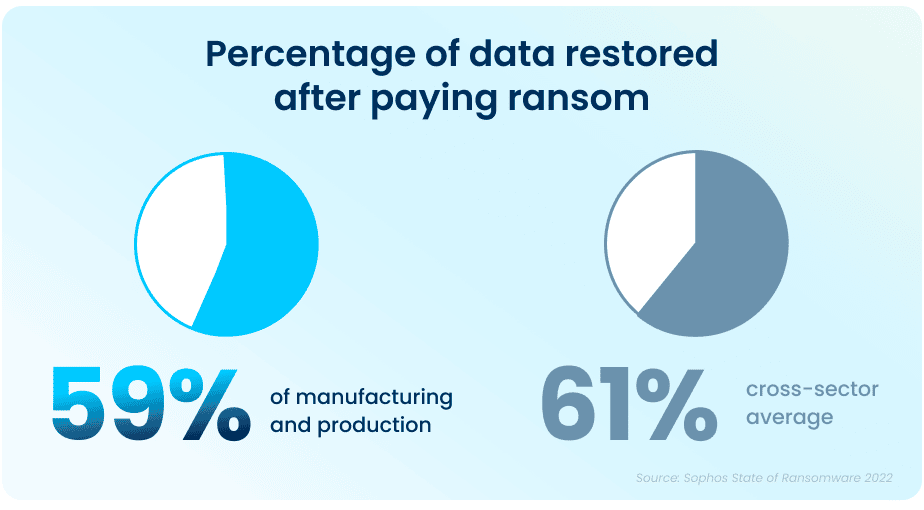
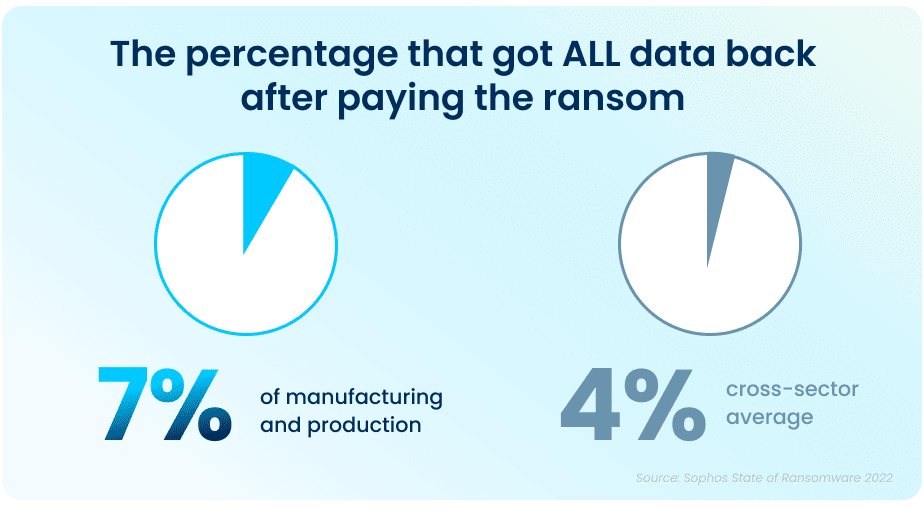
Unfortunately, while paying a ransom typically allows organizations to get some data back, it is proving to be less effective than in years past. On average, in 2021, organizations that paid a ransom only got back 59% of their data, and only 7% of those that paid the ransom got ALL of their data back. This highlights the importance of employing multiple methods to restore data—utilizing backups in particular can improve the speed of recovery and increase the amount of data that can be recovered in the event of an attack.
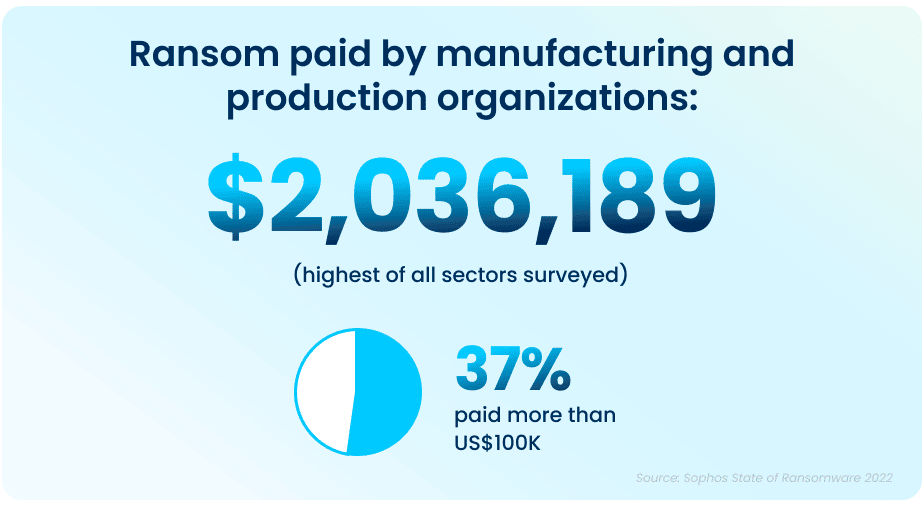
Ransom Payments Have Increased
The average ransom pay-out has seen an exponential increase from what was reported in 2020 data, rising from an average of $147K (USD) to a jaw-dropping $2,036,189 (USD) in 2021.
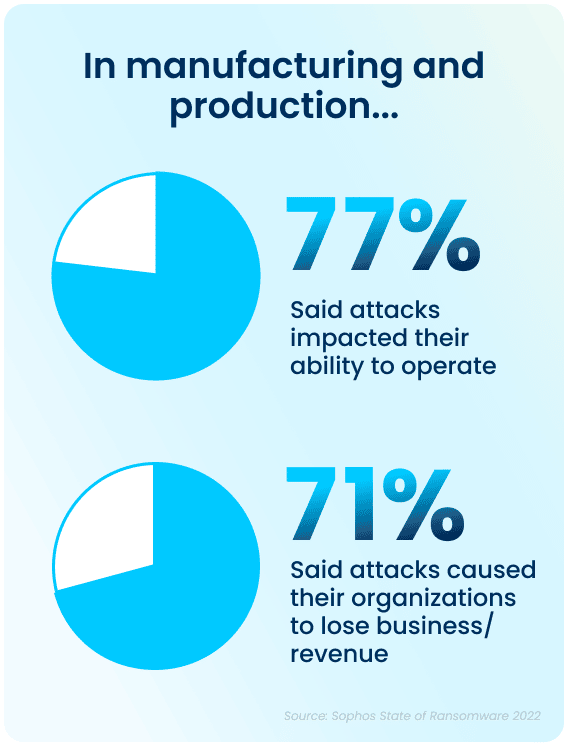
Ransomware Has a Massive Impact on a Company’s Financial Status and Operational Capacity
Even when some of the encrypted data is restored after a cyber-attack, there are additional costs in the form of lost productivity and a decline in operational capacity, which can have a considerable impact on your company. Of those hit by ransomware last year, 77% said their most significant attack impacted their ability to operate, while 71% said it caused them to lose business and/or revenue. The average cost to remediate an attack in 2021 was $1.23M (USD), down from $1.52M (USD) in 2020. This was due in part to cyber insurance providers being able to better guide victims through an effective response more rapidly.
Although there have been improvements in total recovery time over the years, it still took, on average, one week for manufacturing and production organizations to fully recover from the most significant attacks.
Despite the huge economic costs of ransomware attacks, many organizations are continuing to put their faith in defenses that don’t actually prevent ransomware—only more quickly mitigate its effects. Most of the organizations in the survey who weren’t hit by ransomware in the past year and didn’t expect to be hit in the future cited backups and cyber insurance as reasons why they don’t anticipate an attack. It’s important to note that neither of these elements can actually prevent cyber-attacks.
Simply having security mitigation resources in place does not mean that they will be effective against malicious attacks. Despite having ample resources—in both personnel and technology—organizations will not achieve a high return on investment without a combination of the right technology and expertise to use the technology effectively.
Cyber Insurance Drives Changes to Cyber Defenses
Thankfully, organizations do not have to shoulder the burden of ransomware costs all on their own. The survey found that three out of four manufacturing and production organizations had insurance against ransomware attacks. Organizations that had been previously hit by ransomware attacks in the past were much more likely to have cyber insurance coverage against ransomware. However, many respondents indicated that securing coverage has changed or gotten more difficult to obtain in the past year:
- 56% said the level of cybersecurity they need to qualify is now higher
- 53% said policies are now more complex
- 42% said it is more expensive
- 35% said fewer companies offer cyber insurance
- 30% said the process takes longer
As a result, 97% of organizations that have cyber insurance have made changes to their cyber defenses to improve their cyber insurance position. 70% have implemented new technologies and services, while 63% have increased staff training and educational activities, and 59% have changed processes and behaviors.
But It Doesn’t End There
The State of Ransomware 2022 survey by Sophos has revealed that ransomware continues to be an imminent threat for the manufacturing and production industry. For many, choosing an experienced partner with expertise in cybersecurity not only improves their chances of getting approved for the right amount of cyber insurance coverage, but can also ensure that companies see an higher return on investment and improved ability to both prevent and mitigate attacks in the future.
Poor Document Sharing Strategies May Share Too Much Information with Bad Actors
To share documents across your organization, it may be as easy as making a single click—but that doesn’t mean they are protected from malicious actors with bad intent. One mistake and you could be leaving holes in your security fabric, allowing hackers to access your company’s shared documents.
While file storing systems are a popular and useful solution, it can be dangerous to allow everyone in your company unimpeded access to everything they contain. Important company information, and many different files, live within document sharing applications—everything from job applications and budgets to employees’ personal information—which can make them a target for hackers. Document sharing applications can be risky if your company’s security and security training are not up to speed.
How can your organization ensure shared documents remain secure?
When looking to keep your document sharing application secure there are rules you and your employees should follow to ensure quality cyber security. A few of these rules include:
1. Use a password manager
A password manager can users track a multitude of passwords, allowing for a different, complex password for each work (or personal) login and account the user maintains. Utilize this idea to organize your passwords, maintain difficult to guess passwords, and keep track of each one in a secure digital location.
2. Enable multi-factor authentication
Multi-factor Authentication (MFA) requires you to perform a secondary action to finish logging into an account. MFA sends a message to a phone, or another device, providing you with a code that is needed to successfully log into your account. Without this code, anyone who has attained access to your email account cannot succeed in logging into your company’s network, even if they change your password and attempt to log in again.
3. Be choosy
Take the time to choose who can, should, and needs access to specific files and folders. If access is not essential to someone’s job, consider limiting their access to non-relevant portions of your document sharing solution. Removing access to HR or accounting files from someone who is in marketing may be a good choice to make. If someone needs a file from a location they do not have access to, many document sharing solutions allow you to create a link that expires after a certain amount of time. This link will only allow the receiver to view the file they need access to while they need access to it. After the link expires, the receiver will no longer be able to view the file.
4. Provide regular security awareness training
Regular cyber security awareness training sessions allow your employees to learn about new security concerns, kinds of attacks, and now to keep your organization safe from bad actors. Training employees to look for the signs of phishing, malware, ransomware, hackers, and security holes helps keep document sharing applications safe and secure.
When done right, document sharing is incredibly useful to every business, and can be done successfully by putting a little bit of extra effort into your cyber security planning. An experienced security partner can help keep your business safe from outside threats, allowing you peace of mind that your important files are secure and encrypted from bad actors.
Aunalytics, a secure managed services partner, can help you with everything from managing your IT services, to functioning as your SOC, and also provides advanced security services. With a focus on helping mid-market clients, Aunalytics works with you, step-by-step, to help you succeed your security goals.
How To Improve Your Company’s Security Awareness in 2023
We’ve almost made it through 2022, and with every year that passes cyberattacks become more targeted and deceitful. If your organization does not have a Security Awareness Training program in place, you may not know there’s a lot in the digital world that can cause severe distress to you, your coworkers, and your day-to-day operations. Long gone are the days where all we had to be wary of was an email asking you to help a Nigerian prince with their boatloads of money. Technology has come a long way—and so have bad actors trying to get access to your data and disrupt your business operations. Fortunately, there are ways to mitigate these risks.

Social Engineering Attacks
Spam and phishing calls, texts, and emails are everywhere we look—or hear—and these individuals craft their messages in the most believable ways. A relative in the need of some help or your supervisor asking you to buy some gift cards are some of the most common forms the phishing and spam messages might take. The constant barrage of threats requires you to keep a vigilant and informed eye on them. Before a bad actor can get access to the entire company’s vital data, an individual working in that company usually experiences an attack. The victim could be the CTO of a company, a receptionist, or the new intern—anyone is under the risk of a social engineering attack.
Scammers, hackers, and all other types of bad actors in this era of information technology are getting smarter, and we need to pull up our socks and get informed. It’s predicted that, by 2025, there will be an average of 10 devices per person, all connected to the internet and at risk of cyberattack. These devices need to be guarded—not only by cybersecurity services, but also by individual employees.
There are several types of threats out in cyberspace that bad actors deploy to gain access to an organization’s valuable data. The most common and widespread attacks are phishing, spear phishing, vishing, and smishing. Don’t be fooled by the names— these kinds of attacks pose a great deal of trouble unless they can be spotted before they have a chance to coerce or convince someone to unknowingly hurt their organization.
Phishing happens in the form of an email with malicious links or attachments that, if clicked, could give bad actors access to your system or persuade someone to divulge personal information in the form of passwords or credit card numbers. Spear phishing is a highly targeted form of phishing, aiming to attack and exploit one specific person. Spear phishing attacks typically include personal information about you that bad actors can find on social media or other online public forums. Smishing and Vishing are also phishing but in the form of a text message or a phone call.
Employees Can Fight Back By Getting Informed
Employees will need to be able to spot certain indicators that should make them pause before making a decision that might cause a security breach. Often, something will seem out of place with a phishing message, but your employees cannot know what to look for if they aren’t trained to see signs of malicious intent. Vigilance is critical in this scenario because bad actors are making sure that these markers are very difficult to spot. The information below can help employees begin to spot red flags:
- Phishing through emails is the most common form bad actors choose to work with. The following points might not seem like much at first glance, but, if combined, these are a sure sign of a phishing attack:
- Subject lines that have a sense of heightened urgency;
- From unknown and/or unexpected email addresses;
- Different ‘reply-to’ and ‘from’ email addresses;
- Unusual days and times for the email to have been sent—like after work or extremely early on a Saturday;
- Clearly noticeable grammar and spelling mistakes;
- Unnatural wording;
- Unexpected or suspicious links or attachments; or
- An offer for a reward in the form of money or gift cards in exchange for an action that that needs to be taken.
- Text messages also open organizations and people to the same security risks as emails, even though they are a different format. In the case of smishing, most of the red flags for phishing apply, but there are a few more that individuals should take note of:
- The sender claims to be a company executive or direct report with an urgent need;
- The number is different from the number that you might have saved;
- Enquiring about personal information;
- Requesting to follow a link or send money.
- Vishing attacks, or phone call scams are very prevalent and commonly tend to prey on the elderly. These are mainly seen outside the workplace, but they do still pose a threat. The following are some common signs people need to look out for in the case of a vishing attack:
- Unexpected calls from unrecognized numbers;
- Caller requesting access to a digital device to solve an issue;
- Caller threatening legal action and claiming to be from a government body, like the IRS;
- Caller claiming you are a prize winner;
- Caller requesting money in the form of gift cards or asking for personal information like bank details and credit card numbers;
- Caller impersonating an executive, co-worker, or even a family member has found themselves in deep, generic trouble—like getting into a car accident or being arrested—necessitating immediate cash transfers, money wires, and more to get them out of trouble or harm’s way.
Organizations should put a Security Awareness Training program in place to help their employees gain knowledge and experience a behavioral transformation, which would further impact their ability to avoid causing breaches in your organization’s network. Such initiatives ensure everyone in the company is aware of the risks that exist in the digital landscape, and they make decisions that are in the best interests of the organization’s overall security. Each employee is responsible for their organization’s cybersecurity, and if they treat all the information they have access to as a section of the overall information system, the overall system will have significantly higher chances of being secure. If your organization would like to learn more about implementing a Security Awareness Training program, contact Aunalytics today.
The Value of Data Visualization
In this brief video, Dr. David Cieslak, Chief Data Scientist at Aunalytics, discusses the value that data visualization brings to data analytics. Whether you’re using a simple tool such as Excel or a BI software such as Tableau, creating a visual representation of your data allows it to be consumed by a much broader and less technical audience. Whether you’re a marketing specialist, a loan officer, or a bank president, a well-designed and up-to-date dashboard greatly improves your ability to understand and work with your data in a way that lists and spreadsheets can’t.
Aunalytics’ Daybreak Dashboards for Financial Institutions offer a variety of data visualization options such as the Customer Profile dashboard, which provides a 360-degree view of each customer, the Lending KPI dashboard, which provides overall and detailed lending performance across your organization, and the Marketing KPI dashboard, which allows for targeted campaigns to reach the right customer at the right time with the right product. With Aunalytics, you get the technology and the expertise required to turn your disparate data into easily understandable insights through the Daybreak Dashboards.
David Cieslak, PhD, is the Chief Data Scientist at Aunalytics since its inception and leads its Innovation Lab in the development and delivery of complex algorithms designed to solve business problems in the manufacturing/supply chain, financial, healthcare, and media sectors. Prior to Aunalytics, Cieslak was on staff at the University of Notre Dame as part of the research faculty where he contributed on high value grants with both the federal government and Fortune 500 companies. He has published numerous articles in highly regarded journals, conferences, and workshops on the topics of Machine Learning, Data Mining, Knowledge Discovery, Artificial Intelligence, and Grid Computing.
How An End-to-End Analytics Solution Helps You Avoid Hidden Costs
As the new year approaches, digital transformation should be at the top of every mid-market organization’s to-do list. As organizations begin to understand the value of business analytics for their daily operations, the need for an end-to-end analytics solution becomes evident. Yet, many companies struggle to obtain the right analytics solutions to fit their specific needs.
Unfortunately, the analytics solution market can be difficult to navigate. Since building an analytics tool in-house is incredibly time-consuming and very costly, many mid-market companies would be better served by working with a solution provider who can provide both the tools and talent necessary to achieve their business goals.
Digital Transformation Roadblocks
One major roadblock in the pursuit of digital evolution is determining how much an analytics solution is going to cost. Analytics solutions are complex, and when an analytics company gives a quote, they often fail to mention additional add-ons their solution needs to be functional. For instance, charges for a third-party cloud to host your analytics solution and individual charges for connectors that allow your disparate data sources to flow into the solution are the most common up-charges.
Your organization could get stuck with unexpected licensing fees or overage charges from a third-party cloud provider. Worse yet, you may end up piecing together various technologies, while lacking the adequate technical talent to keep the solution functioning and show actionable results. To achieve value from your investment, it is vital to look for a partner that can provide you with a solution where extra charges do not come into play. Budgets are an integral part of the decision-making process when it comes time to choose a solution provider.
With hidden costs, figuring out how a particular solution is going to fit into your budget becomes increasingly difficult. The most effective solution is opting for a partner who can provide your company with an end-to-end analytics solution.
Why Mid-Market Organizations Need End-to-End Analytics Solutions
To compete with larger institutions, mid-market organizations need to leverage their existing local data to gain insights to better serve their clients. An end-to-end solution ensures you do not end up with a solution your team cannot utilize to achieve your business goals and thrive in an increasingly competitive market.
It is a known fact that mid-market businesses struggle with retaining talent for data management, IT, security, and advanced analytics. Opting for an end-to-end solution gives you access to a team of experts who will always be by your side, assisting you every step of the way.
With Aunalytics, you get the technology and the expertise required to complete your journey from disparate data to actionable business results. Using our platform, your entire organization can reap the benefits of having a reliable and robust data platform.
Aunalytics Provides a Complete, End-to-End Analytics Solution for Mid-Sized Organizations
Aunalytics offers an end-to-end analytics solution that includes the right technology paired with experts who work by your side to help you accomplish your business goals. The technology, combined with the technical talent necessary to fully utilize it, will help your organization achieve true value from your investment. End-to-end analytics solutions provide you with insights from your data so you can concentrate on critical business decisions. No longer do you have to worry about overages, licensing costs or other additional charges. Aunalytics has the answers to your business and IT questions.
The Aunalytics Data Platform is a robust, cloud-native data platform built for universal data access, powerful analytics, and AI. It includes the following components:
- Aunalytics Enterprise Cloud provides a highly redundant, secure, and scalable platform for hosting servers, data, analytics, and applications at any performance level.
- Aunsight Golden Record integrates and cleanses siloed data from disparate systems for a single source of accurate business information across your enterprise.
- Daybreak Analytics Database provides daily insights powered by Artificial Intelligence (AI) and Machine Learning (ML) driven analytics, industry intelligence, and smart features that enable a variety of analytics solutions and timely actionable insights that drive strategic value across your company.
This end-to-end platform enables your business to extract answers from your data without having to worry about additional charges that might break your budget. Our solutions are secure, reliable, and scalable, all according to your business’ needs. Aunalytics solutions seamlessly integrate and cleanse your valuable data for accuracy, ensuring data governance and employing Artificial Intelligence (AI) and Machine Learning (ML) driven analytics to glean customer intelligence and timely actionable insights that drive strategic value.
Using our solution, team members across your organization can reap the benefits of having an end-to-end analytics solution to make data-driven decisions. Company executives can view data cleansed into an accurate golden record that is streamed in real-time to enable better decision making for the entire organization. Your organization’s marketing team can have access to aggregated data that reveals a 360-degree view of your customer, including insights into customer behavior, that empowers them to run data-driven campaigns to the right customer, at the right time, with the right product. Your IT department can ensure that you are functioning at peak efficiency by analyzing the data collected to scale resources and identify potential roadblocks and bottlenecks. Those are just a few departments that would benefit—think about how powerful a real-time analytics solution could be across your entire organization.
Increasingly Difficult Security Requirements Complicate Cyber Insurance Renewal
Have you received a cyber insurance renewal notice with a shocking sticker price? With an ever-increasing number of security incidents involving data breaches, ransomware, phishing scams and more, the cyber insurance landscape has changed. It’s no longer possible to get premium discounts for implementing certain security controls—more is now required. And, without enhanced security measures, you may not get cyber insurance at all.
Threats evolve over time, meaning your security posture needs to evolve in order to not only remain operational, but also be compliant to qualify for most insurance policies.
Insurance companies are now requiring more precautionary measures than ever before due to the constant—and costly—increase of threats. Premiums are increasing and coverage is being denied even for companies that have no history of breaches or claims—cyber insurance renewal rates have increased by up to 200% over the past two years, even for companies who have not made any claims.
The average cost of a data breach has raised from a massive $3.86 million in 2020 to a staggering $4.24 million in 2022.
The Solution

With the risks of operating in an increasingly digital world, cyber insurance is essential for your business to function and remain protected in the event of an attack. Aunalytics’ Advanced Security experts have the talent and technology to audit your security and discuss precautionary measures an insurance company may want you to take before renewal. With a dedicated team, your business can avoid costly data breaches, ransomware, and get your security up to snuff.
Are you ready to assess your security before your company is the victim of a bad actor, costing you upward $4.24 million dollars? See if an audit by our security experts makes sense, and whether your insurance company has outright dictated (or hinted by their renewal questionnaires) new precautionary measures that they expect your enterprise to adopt to obtain coverage.
Daybreak Allows Financial Institutions to Increase Wallet Share with Competitor Payment Smart Feature
In the competitive financial services landscape, increasing revenue through new customer acquisition alone is a challenge. According to the Harvard Business Review, it can be anywhere from five to 25 times more expensive to acquire a new customer than to retain an existing one. While new customer acquisition is important, retention and expansion of existing relationships should be a high priority—especially during economic downturns when reducing costs is imperative. A recent report by Bain & Company states, “In financial services, a 5% increase in customer retention produces more than a 25% increase in profit. Why? Return customers tend to buy more from a company over time.” Therefore, it makes sense for community banks and credit unions to focus on retention and increasing wallet share of existing customers.

Winning Back Business by Identifying Competitor Payments
Many community bank customers and credit union members utilize multiple financial institutions for various products. They may have a checking or savings account at their local bank or credit union, but an IRA account at a large, national investment firm, or a loan through another financial institution. By identifying which customers have external accounts and which products they may have through other institutions, community banks and credit unions can take steps to win back that business and increase wallet share of their existing customers and members. Daybreak‘s Competitor Payments Smart Feature mines transactional data and uses AI algorithms to flag external products with competing financial institutions on all active customers/members. These insights can be used to make more attractive targeted offers to win back business.
Watch the video below to see how banks and credit unions can utilize Daybreak’s Competitor Payments insights to win back business from competing institutions:
In addition to providing the ability to discover competitor payment insights in transactional data, Daybreak allows community banks and credit unions to compete with large financial institutions by…
- Understanding customers,
- Optimizing processes, and
- Revealing actionable insights.
See how Daybreak Customer Intelligence for Financial Institutions is the customer data platform that makes it easier for community banks and credit unions to gain actionable insights and achieve positive business outcomes.
Cloud or On-Prem Servers—Which Is Better for Your Company?
Every organization needs to manage its data to get its desired business outcomes. For a company to access its data and use it in day-to-day operations, dashboards, reporting, and data analytics, it either needs a cloud or on-premises solution to facilitate compute, storage, and data management strategies.
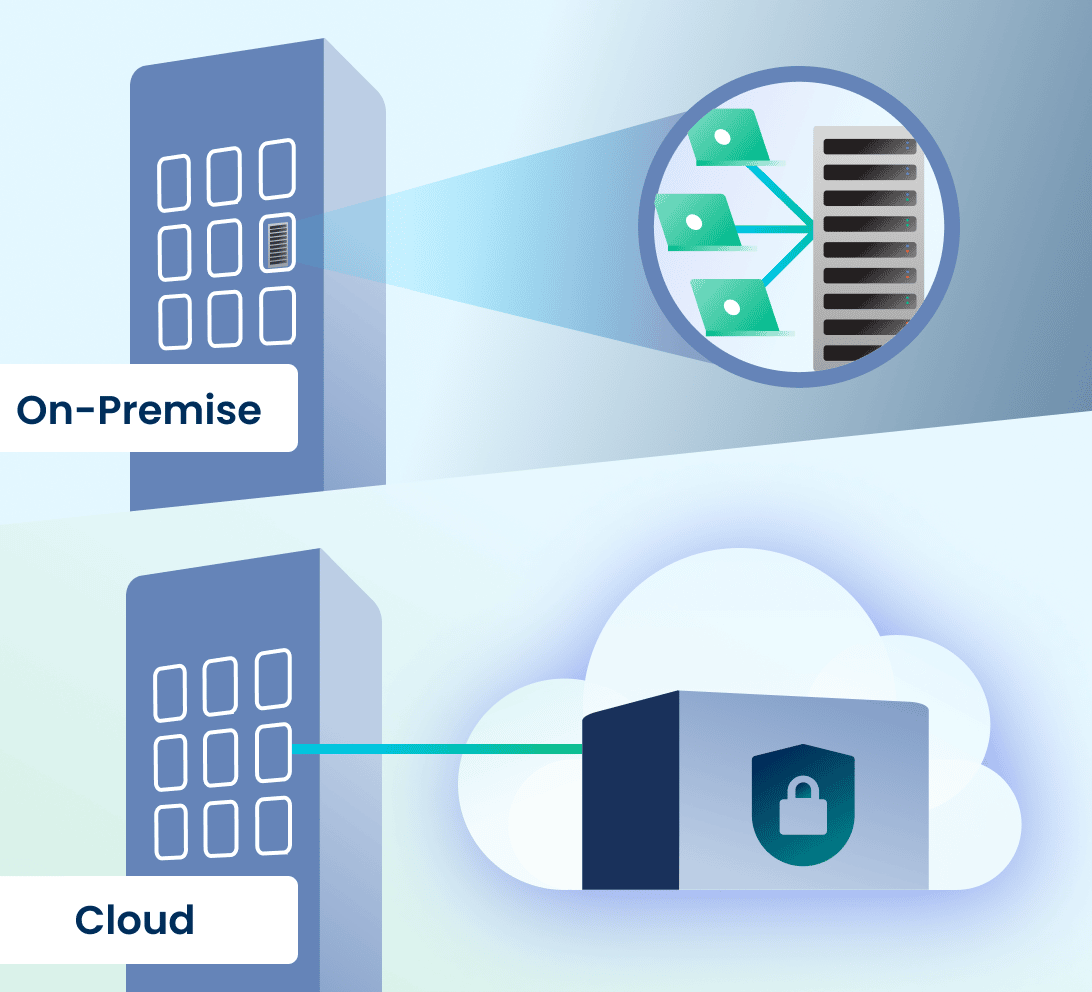
What’s The Difference Between The Cloud And On-Premises Data Storage?
An on-premises data server is hardware that you maintain on your company’s premises for storing, processing, and accessing information through your organization’s networks. An in-house IT department is needed to maintain, turn over/replace, and upgrade the hardware, keep it stable and operational, and secure it.
A cloud storage solution run by an expert and backed by a cutting-edge data center provides the same functions as an on-premises server and more. It does not exist on your company’s premises and the data on it is accessed through the internet. All updates and maintenance tasks are performed by the cloud provider, who owns and operates its own hyper-secure data centers to safeguard your data in case of failure, cyberattack, or outage. Like on-premises servers, access to cloud data can be set by administrators to be permission-based to allow access only by authorized personnel.
On-Premises vs. Cloud—Which Option Best Suits Modern Business Needs?
There are more factors when choosing between using a cloud computing solution or keeping servers on-premises, including customizability and scalability, security concerns, and the budget for your organization’s data management strategy. While on-premises data servers regularly require hardware upgrades in your physical locations to expand alongside your business’s growing needs, a cloud storage and computing solution with access to highly advanced data centers is scalable based upon your workload. Unlike an on-premises server that can take a lot of time and money to set up and ready for operation, cloud service providers ensure you can access your cloud for computing and storage needs almost instantly.
In some mid-sized companies, server rooms tend to be used for multiple purposes, which means that they are sometimes unlocked, unsecured, and allow for unauthorized access that compromises data security. Many mid-sized companies do not have 24/7/365 monitoring of their server rooms, specialized climate controls needed for a data center, and do not consistently deploy or regularly schedule hardware upgrades to keep the systems reliable before something goes down.
One mid-market employee shares the story of a server closet that her company had in a previous workplace. For starters, it could be accessed by nearly every employee of the company. She recounted that the IT department placed portable dehumidifiers in the room to keep moisture down. The IT department’s regular practice was to empty the server closet dehumidifiers in the office’s kitchen sink. Unfortunately, a new IT employee happened to trip while carrying one of the dehumidifiers and spilled water all over the server room. Every employee of the company was affected—they found out that the work they had done since the last backup, which happened to be 5 days ago, had disappeared. Even worse, their servers were down for several days after the incident, further impacting their daily business operations.
Although in the past, people feared that cloud would not be secure, or a company would lose control over its data—cloud has proven to be more secure than on-premises hardware. First, cloud vendors host their own data centers and because this is their main business, they have cutting-edge climate control environments to protect their clients’ data. Cloud vendors adhere to frequent hardware replacement turn-over schedules to keep uptime maximized and cloud operations state-of-the-art. Cloud vendors monitor their data centers 24/7/365, are security experts, and have strict controls in place in order to service clients in highly regulated industries with rigorous data security needs. For most mid-sized businesses, it is more cost effective to rely upon the expertise of a cloud vendor for data security and uptime than to host and maintain its own servers, stay on top of the latest security threats, and staff its data center (or data closet) for monitoring to prevent downtime and security breaches.
Large enterprises often can afford to build their own data centers providing them an alternative to an external cloud provider. However, this is incredibly expensive and can set organizations back by USD $10-25 million on yearly setup and operation costs. This infrastructure also takes a lot of time to be implemented and in today’s fast-paced business environment, this might not be entirely acceptable for decision-makers.
Yet, even for enterprises, on-premises solutions no longer make the most sense. Most modern business applications are cloud-native. Cutting-edge data analytics solutions are cloud-native and connect and integrate data sources using cloud technologies. Clouds are better suited for analytics than on-premises hardware, due to scalability and ability to absorb compute spikes (instead of having to invest in hardware with capacity for compute spikes as machine learning algorithms converge—which leads to excess capacity at other times).
According to Insights for Professionals, 63% of senior IT leaders and company executives who were surveyed expected to invest in cloud infrastructure-as-a-service in 2022. Considering the state of on-premises servers, which are becoming an obsolete technology that require an IT department to keep a constant eye on it, cloud technology is a natural progression in infrastructure for better data management. Gartner reports by 2025 almost 85% of companies will have moved to a cloud-first approach. Cloud technology has now evolved to a point where it provides better stability and security at a more economical price than on-premises solutions.
Mid-Market Company Considerations
Many organizations are operating in hybrid and multi-cloud environments. This means that they have some data in on-site servers, some data in cloud based line of business applications (relying on the application provider for data storage in whichever cloud the application vendor uses for its product), and many have some data in a public cloud.
However, mid-market companies have added considerations when choosing a cloud solution. Most public cloud service providers do not offer data management services. You need to do this yourself. Yet, mid-market companies often do not have this expert talent in-house. For success, mid-market companies need a cloud hyper-scaler that also provides data engineering services to build data connectors and pipelines, warehouses, data lakes, and the like. This skill set is different from a typical IT employee. Hyper-scalers—who can help organizations with data management, transform data from disparate sources into a decision and analytics-ready status, and bring transactional data into the forefront using a cost-effective cloud solution—tend to be private cloud vendors. For this reason, private cloud solutions make more sense than public cloud for mid-sized organizations.

A side-by-side partnership with an experienced cloud-native data platform company will have a measurable and positive impact on mid-market company data management strategies, with built-in access to technical resources and experts, so that your company does not need to hire new FTEs to support data management. Rely on the data management companies for data management so that your company can focus on your main line of business.
Aunalytics’ high performance private cloud provides a highly redundant and scalable platform for hosting servers, data, analytics, and applications at any performance level. Aunalytics delivers data management in a side-by-side service model, bringing companies the technology and the talent needed for data management success. To learn more about our Enterprise Cloud solution, click here.
Don’t Ghost Your Network—Begin Your Security Maturity Journey
Is your security keeping up with the rapidly changing threat landscape? If not, your security is becoming more obsolete by the day—and more vulnerable to scary things like hackers and ransomware by the second. When a company is fully protected with the most up to date hardware, software, monitoring, and consistent patching it begins to reach security maturity.
Security maturity is a consistent state of awareness concerning your network security and can only be achieved when you:
- Have an SOC to monitor and remediate threats
- Have looped vulnerability management
- Employ active defense with security intelligence from multiple sources to protect applications, networks, servers and workstations
- Are willing to adapt your security environment to new and changing threats on a constant basis, and more.

Be Proactive
Instead of relying on a passive security model—or worse, waiting until after a companywide infection—take an active role in your company’s security. The main goal of security maturity is to avoid or reduce the number of security incidents haunting your network. It’s kind of like painting San Francisco’s Golden Gate Bridge. As soon as the painting crew gets from one end to the other with a fresh coat of paint, it is time to start again to repaint the bridge. Security maturity requires constant action and change as your organization adapts to protect against the latest evolving threats.
We all observed remote work access change security and IT on a mass scale in 2020, and security changes continue to become more necessary as bad actors and threats become more and more dangerous to your business as it continues to grow and change—and more dangerous for your customers to do business with you.
October WSJ headlines highlight a Chicago healthcare system, one of the largest in the U.S., being the victim of ransomware that is forcing it to shut down electronic records, systems, and cancel patient appointments. It is now working with law enforcement and outside cybersecurity experts to remediate. A security maturity journey is hard to make on your own, and a good partner can ensure you are meeting the highest security standards possible. Here at Aunalytics, we include security in everything we do because we believe it is a basic building block of IT.
Find A Trusted Security Partner
Without a secure network, you cannot even begin to consider moving further into a security maturity journey. Fortunately, a partner can give you the peace of mind that you will be working with a talented security team that is watching your network 24/7/365, helping to ensure bad actors are caught and eradicated before your company is compromised.
A standard, one size fits all security solution simply doesn’t work anymore—it often leaves cracks, holes, and even chasms for hackers and cyberattacks to slip through. You can improve your journey from cybersecurity to security maturity with a trusted partner.
Click here to learn more.
Ransomware Attacks Pose An Increasing Threat to Businesses of All Sizes: The State of Ransomware 2022
Cyberattacks are a constant threat to organizations of all sizes. To better understand how the current attack environment and track how ransomware trends have changed over time, Sophos commissioned an independent, vendor-agnostic survey of 5,600 IT professional in mid-sized organizations across 31 countries. This survey was conducted in January and early February 2022. The results highlighted the increasing threat that ransomware poses, and the increased role cyber insurance is playing in driving organizations to improve their cyber defenses.
Cyberattacks are up from last year
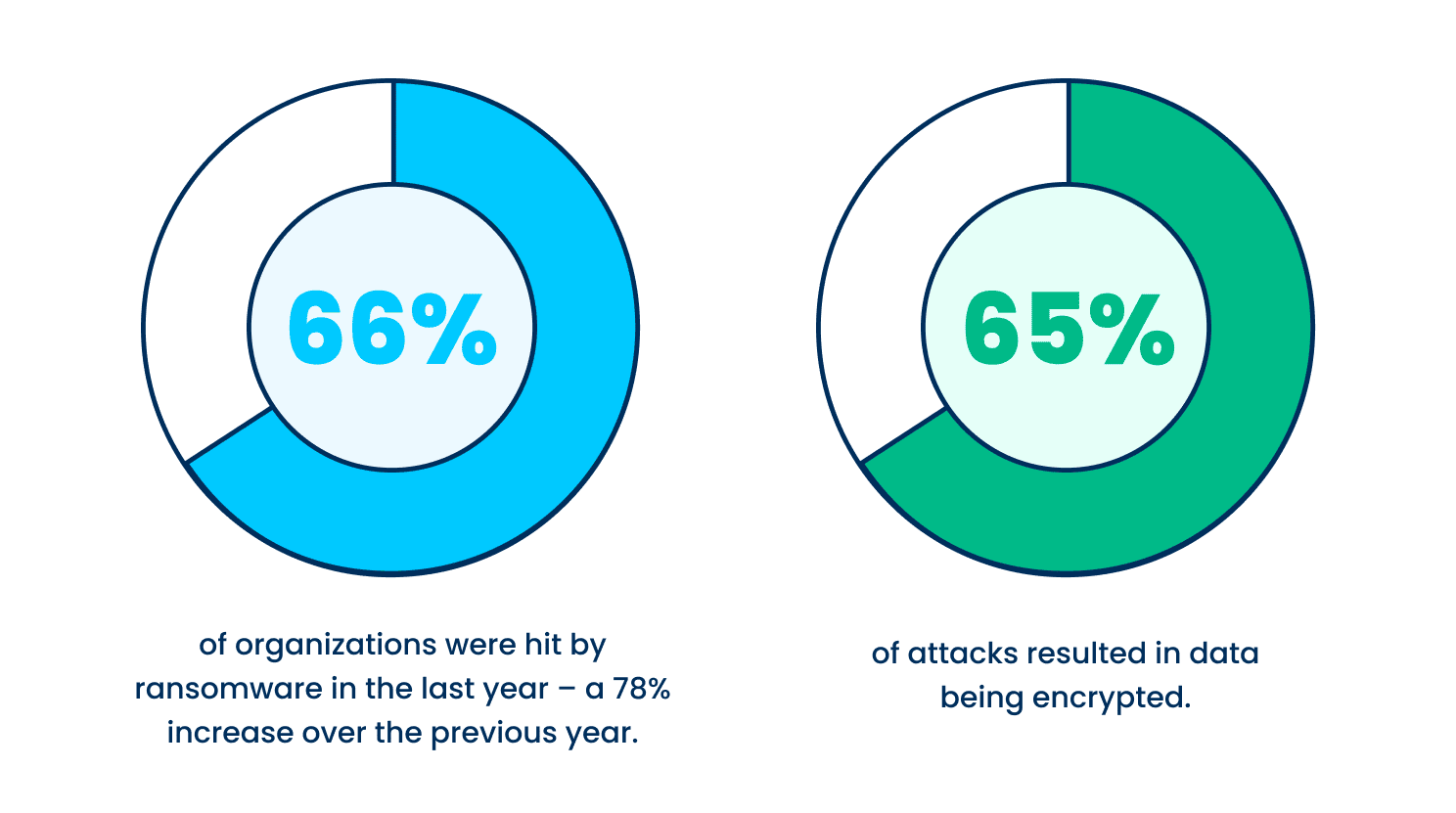
Ransomware attacks have increased significantly over the past year—66% of organizations surveyed were hit by an attack in 2021, up 78% from the previous year. This is due in part to the ease at which bad actors are able to deploy attacks. The Ransomware-as-a-service mode has reduced the skill level needed to attack.
Not only are attacks more prevalent, but the attacks themselves are becoming more successful and more complex. In 2021, 65% of attacks resulted in data being encrypted, up from 54% in 2020. Fifty-nine percent of organizations who experienced cyberattacks saw the complexity of the attacks increase, while 57% saw an increase in the volume of cyberattacks overall.
Data recovery rates are improving
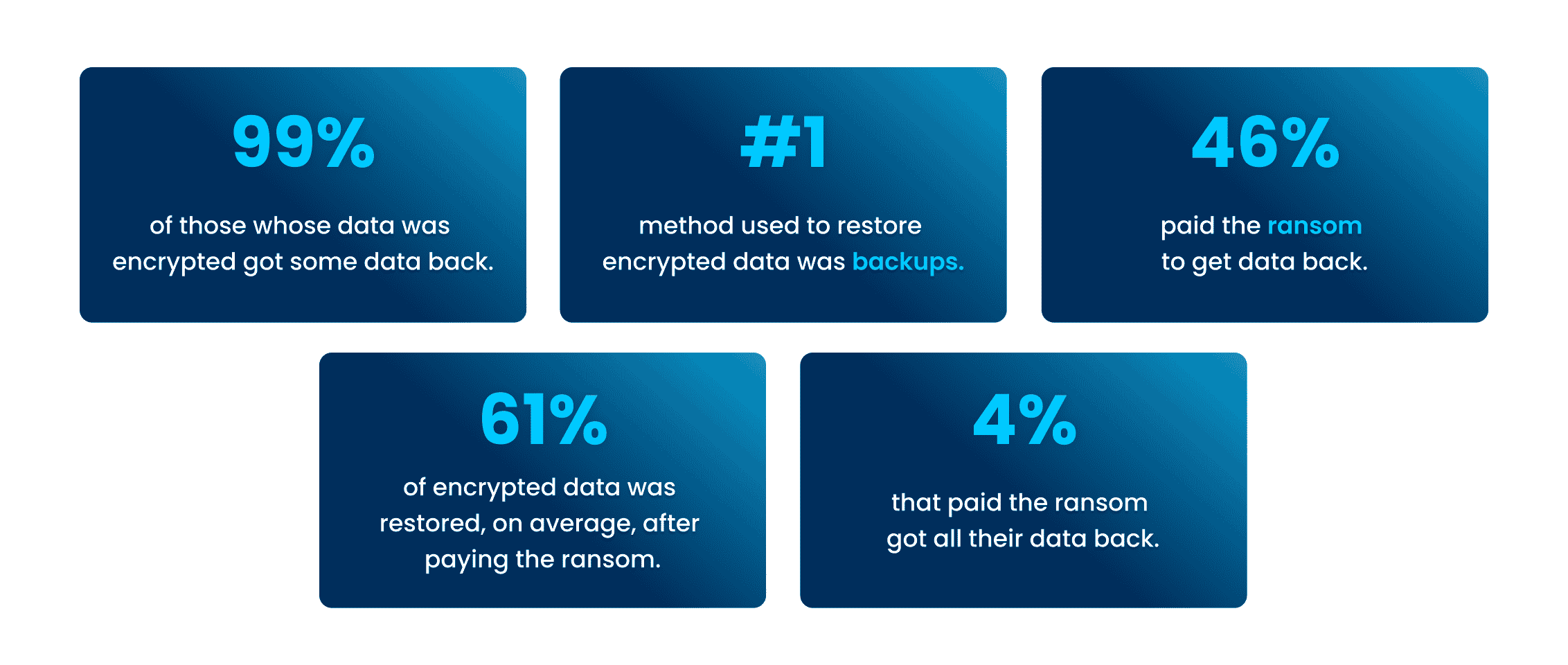
Despite the increase in attacks within the past year, there is some good news. Almost every organization surveyed (99%) were able to get some encrypted data back—up from 96% in 2020. The top method used to restore data was backups, which was used by 73% of organization whose data was encrypted in an attack. In addition to backups, a large portion—forty-six percent—paid a ransom to have their data restored.
Unfortunately, while paying a ransom typically allows organizations to get some data back, it is less effective than in years past at restoring data. On average, organizations that paid a ransom only got back 61% of their data, down from 65% the previous year, while only 4% of those that paid the ransom got ALL their data back in 2021, down from 8% in 2020. This highlights the importance of employing multiple methods to restore data—utilizing backups in particular can improve the speed of recovery and increase the amount of data that can be recovered.
Ransom payments have increased
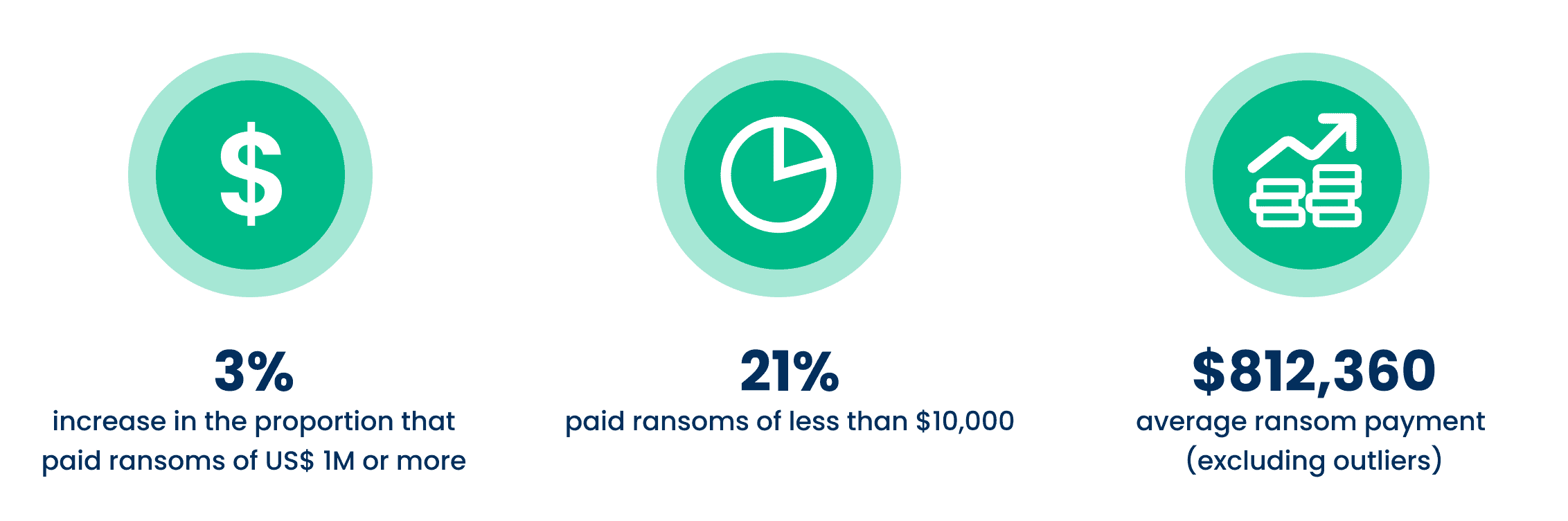
Not only are ransoms less effective at restoring data than in previous years, but the amount of the payments themselves have increased considerably. Between 2020 and 2021 there was a threefold increase in the proportion of victims paying ransoms totaling US$1 million or more. The percentage paying the lowest ransom amounts decreased over that same time—from one in three (34%) to one in five (21%).

The average ransom payout increased 4.8X from 2020 data, from an average of US$170K to US$812,360 in 2021. However, the average ransom amount varies greatly across industries, with manufacturing and utilities coming in at the top of this survey with an average of US$2.04M and US$2.03M, respectively, while healthcare and local/state government had the lowest average ransom payments at US$197K and US$214K, respectively.
Ransomware greatly impacts companies, both economically and operationally
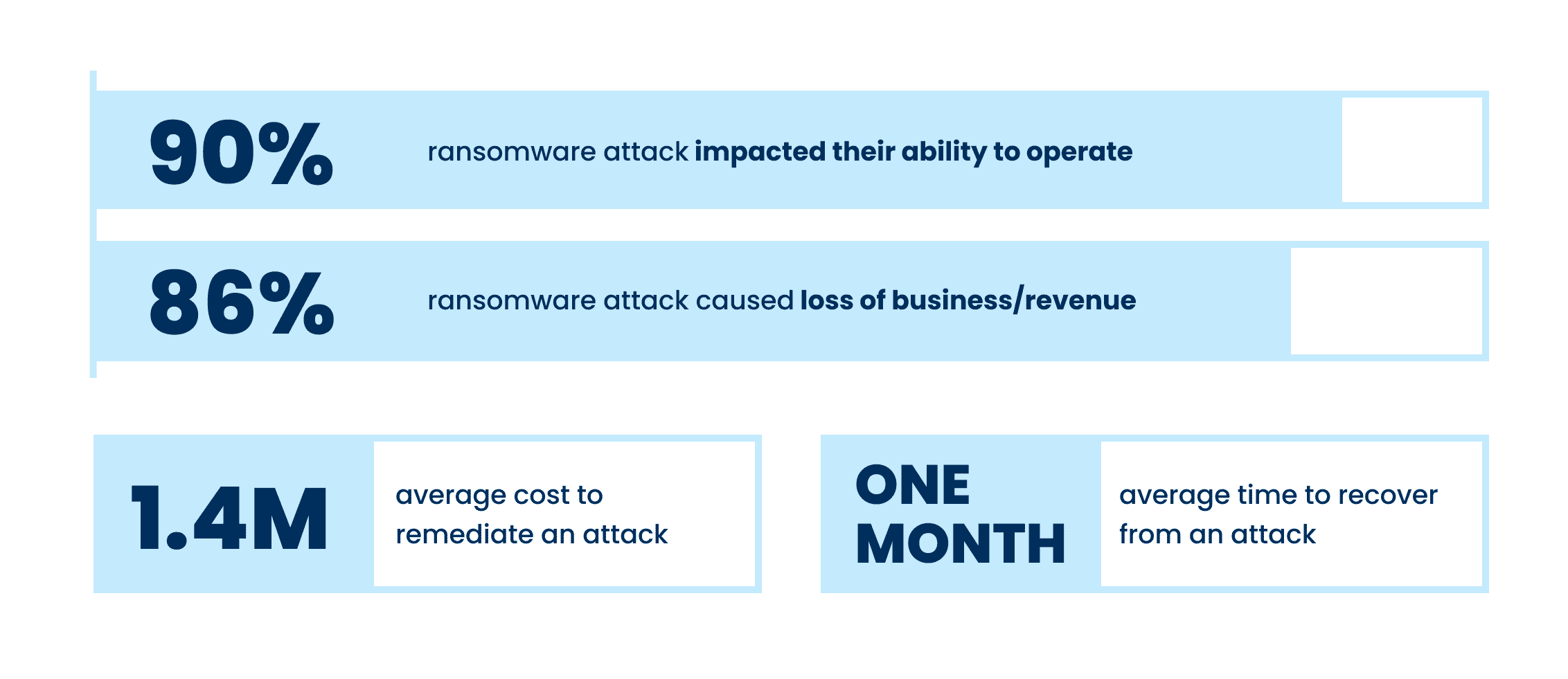
Even when some of all data is able to be restored after a cyber attack, the costs of loss productivity or inability to operate at all can be substantial. Of those hit by ransomware last year, 90% said their most significant attack impacted their ability to operate, while 86% said it caused them to lose business and/or revenue. The average cost to remediate an attack in 2021 was US$1.4M, which, thankfully was down from US$1.85M in 2020. This was due in part to cyber insurance providers being better able to guide victims through an effective response more rapidly.
Although there have been improvements in total recovery time over the years, it still took, on average, one month for organizations to fully recover from the most significant attacks. Those in higher education and central/federal government had the slowest average response times, at around 2-5 months, while manufacturing and financial services were the quickest, with the majority being able to recover in one month or less.
Despite the huge economic costs of ransomware attacks, many organizations are putting their faith in defense that don’t actually prevent ransomware—only more quickly mitigate its effects. Seventy-two percent of organizations in the survey who weren’t hit by ransomware in the past year and didn’t expect to be hit in the future cited backups and cyber insurance as reasons why they don’t anticipate an attack. Neither of these elements actually prevent attacks in the first place.
Simply having security resources in place does not necessary mean that they are effective. Of those surveyed who were hit by ransomware in the last year, 64% said they had more cybersecurity budget than they need, and 24% said they had the right amount of budget. Many of these organization also said they had more headcount or the right amount of headcount (65% and 23%, respectively. This reveals that despite having ample resources—both personnel and technology—organizations will not achieve a high return on investment without a combination of the right technology and expertise to use the technology effectively.
Cyber insurance drives changes to cyber defenses

Thankfully, organizations do not have the shoulder the burden of ransomware costs all on their own. The survey found that four in five mid-sized organizations had insurance against ransomware attacks. However, 34% said there were exclusions/exceptions in their polices. Organizations that had been previous hit by ransomware attacks in the past were much more likely to have cyber insurance coverage against ransomware. However, many respondents indicated that securing coverage has changed in the past year, or gotten more difficult to obtain:
- 54% said the level of cybersecurity they need to qualify is now higher
- 47% said policies are now more complex
- 40% said fewer companies offer cyber insurance
- 37% said the process takes longer
- 34% said it is more expensive
As a result, 97% of organizations that have cyber insurance have made changes to their cyber defense to improve their cyber insurance position. 64% have implemented new technologies/services, 56% have increased staff training/education activities, and 52% have changed processes/behaviors.
Conclusion
The survey has revealed that ransomware continues to be an imminent threat for organizations of all sizes across industries. For many, choosing an experienced partner with expertise in cybersecurity not only improve their chances of getting approved for the right amount of cyber insurance coverage, but can ensure that they see an higher return on investment and improved ability to prevent and mitigate attacks in the future.