Ransomware Attacks Pose An Increasing Threat to Businesses of All Sizes: The State of Ransomware 2022
Cyberattacks are a constant threat to organizations of all sizes. To better understand how the current attack environment and track how ransomware trends have changed over time, Sophos commissioned an independent, vendor-agnostic survey of 5,600 IT professional in mid-sized organizations across 31 countries. This survey was conducted in January and early February 2022. The results highlighted the increasing threat that ransomware poses, and the increased role cyber insurance is playing in driving organizations to improve their cyber defenses.
Cyberattacks are up from last year
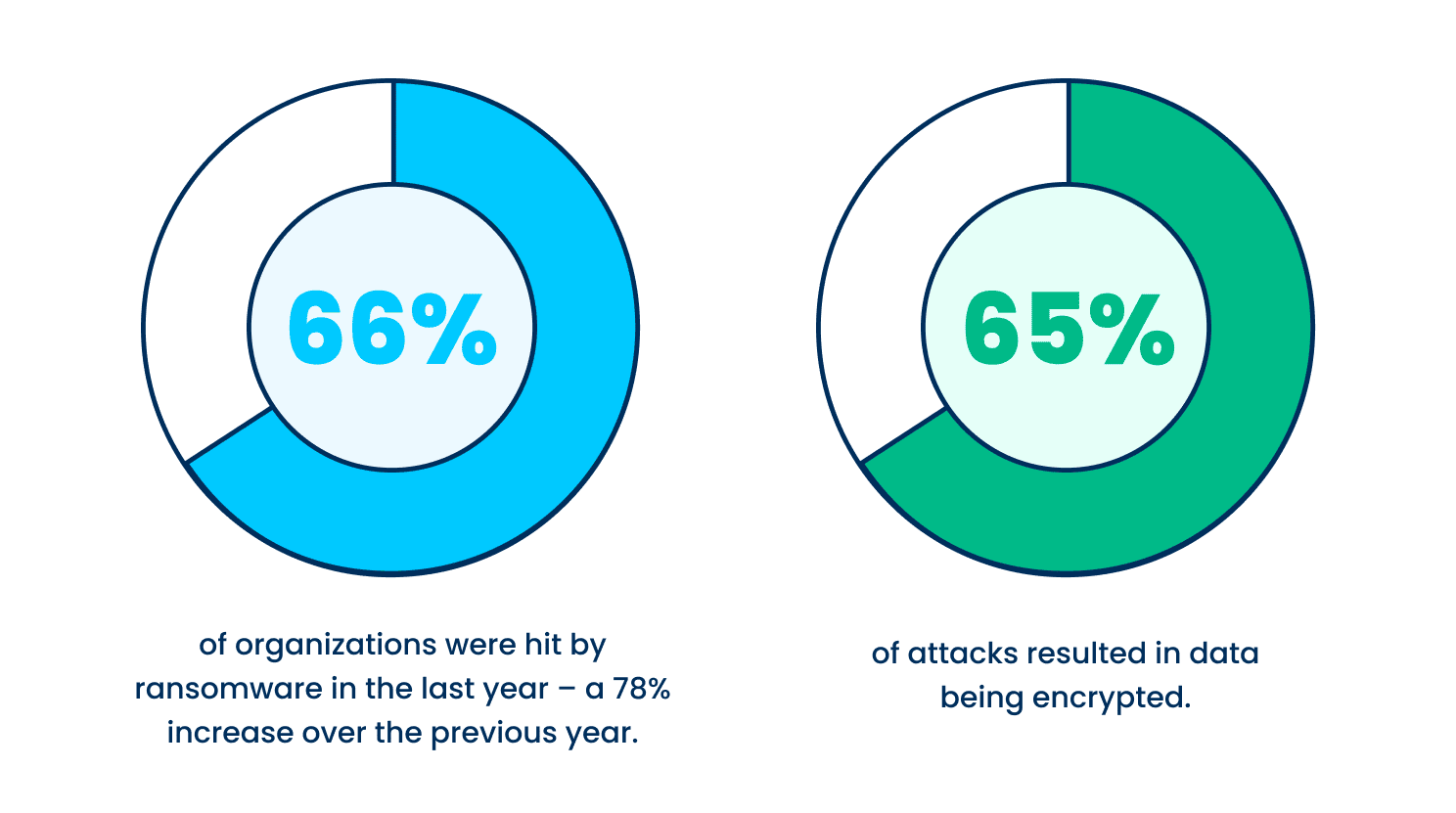
Ransomware attacks have increased significantly over the past year—66% of organizations surveyed were hit by an attack in 2021, up 78% from the previous year. This is due in part to the ease at which bad actors are able to deploy attacks. The Ransomware-as-a-service mode has reduced the skill level needed to attack.
Not only are attacks more prevalent, but the attacks themselves are becoming more successful and more complex. In 2021, 65% of attacks resulted in data being encrypted, up from 54% in 2020. Fifty-nine percent of organizations who experienced cyberattacks saw the complexity of the attacks increase, while 57% saw an increase in the volume of cyberattacks overall.
Data recovery rates are improving
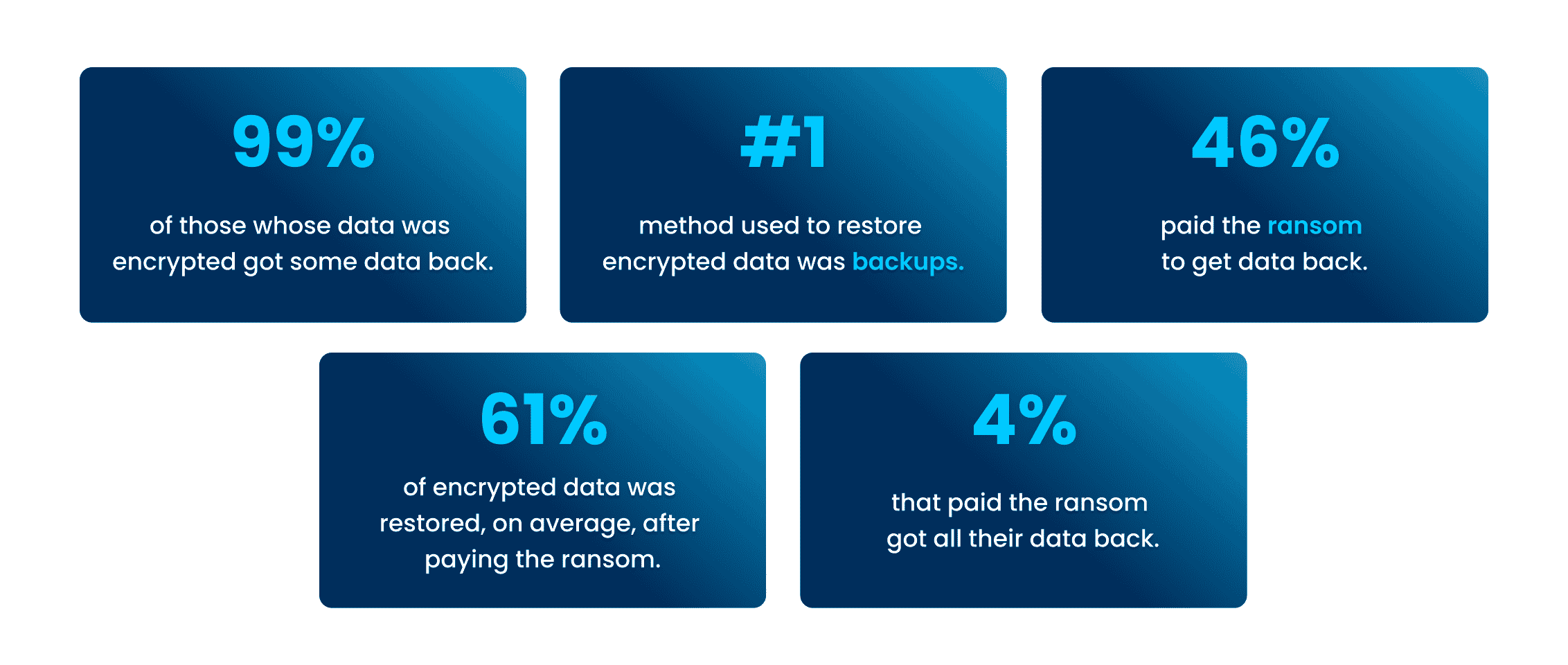
Despite the increase in attacks within the past year, there is some good news. Almost every organization surveyed (99%) were able to get some encrypted data back—up from 96% in 2020. The top method used to restore data was backups, which was used by 73% of organization whose data was encrypted in an attack. In addition to backups, a large portion—forty-six percent—paid a ransom to have their data restored.
Unfortunately, while paying a ransom typically allows organizations to get some data back, it is less effective than in years past at restoring data. On average, organizations that paid a ransom only got back 61% of their data, down from 65% the previous year, while only 4% of those that paid the ransom got ALL their data back in 2021, down from 8% in 2020. This highlights the importance of employing multiple methods to restore data—utilizing backups in particular can improve the speed of recovery and increase the amount of data that can be recovered.
Ransom payments have increased
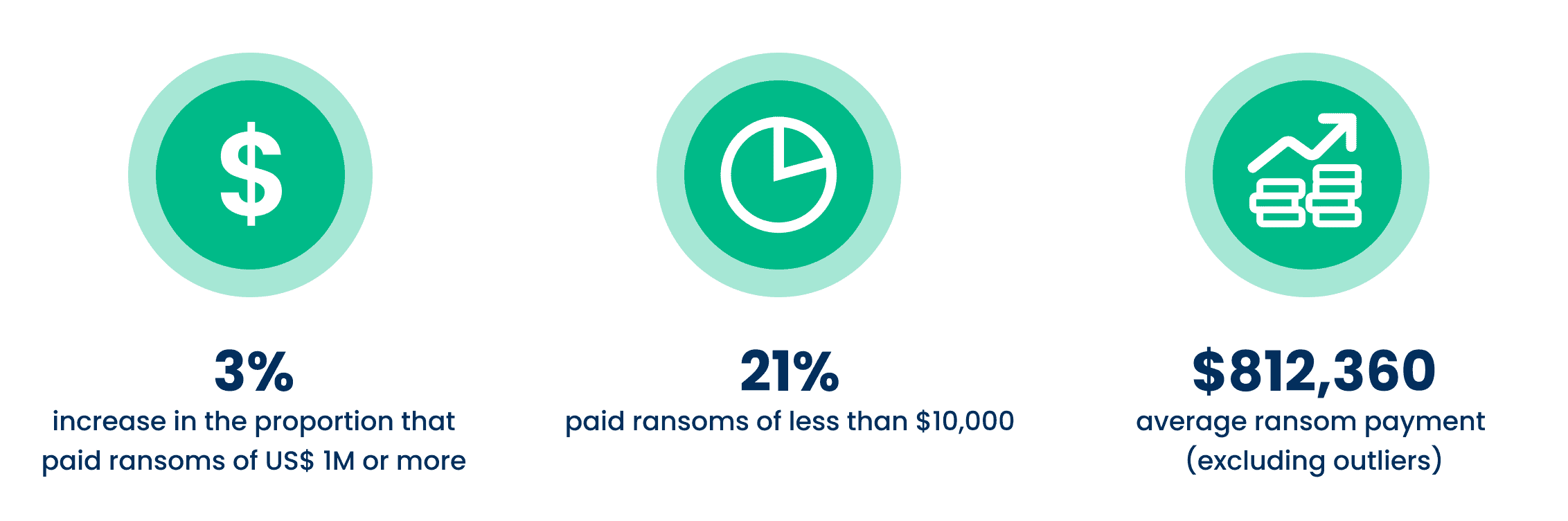
Not only are ransoms less effective at restoring data than in previous years, but the amount of the payments themselves have increased considerably. Between 2020 and 2021 there was a threefold increase in the proportion of victims paying ransoms totaling US$1 million or more. The percentage paying the lowest ransom amounts decreased over that same time—from one in three (34%) to one in five (21%).

The average ransom payout increased 4.8X from 2020 data, from an average of US$170K to US$812,360 in 2021. However, the average ransom amount varies greatly across industries, with manufacturing and utilities coming in at the top of this survey with an average of US$2.04M and US$2.03M, respectively, while healthcare and local/state government had the lowest average ransom payments at US$197K and US$214K, respectively.
Ransomware greatly impacts companies, both economically and operationally
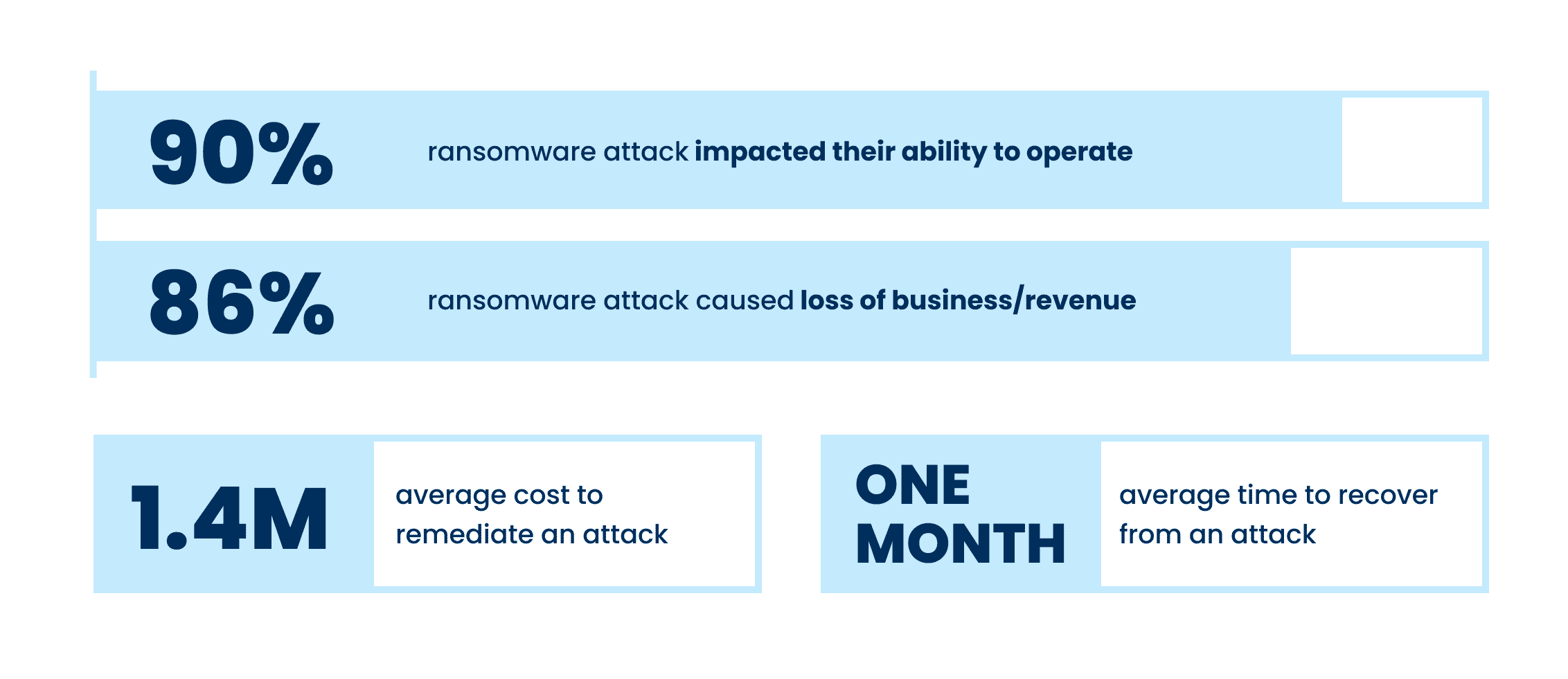
Even when some of all data is able to be restored after a cyber attack, the costs of loss productivity or inability to operate at all can be substantial. Of those hit by ransomware last year, 90% said their most significant attack impacted their ability to operate, while 86% said it caused them to lose business and/or revenue. The average cost to remediate an attack in 2021 was US$1.4M, which, thankfully was down from US$1.85M in 2020. This was due in part to cyber insurance providers being better able to guide victims through an effective response more rapidly.
Although there have been improvements in total recovery time over the years, it still took, on average, one month for organizations to fully recover from the most significant attacks. Those in higher education and central/federal government had the slowest average response times, at around 2-5 months, while manufacturing and financial services were the quickest, with the majority being able to recover in one month or less.
Despite the huge economic costs of ransomware attacks, many organizations are putting their faith in defense that don’t actually prevent ransomware—only more quickly mitigate its effects. Seventy-two percent of organizations in the survey who weren’t hit by ransomware in the past year and didn’t expect to be hit in the future cited backups and cyber insurance as reasons why they don’t anticipate an attack. Neither of these elements actually prevent attacks in the first place.
Simply having security resources in place does not necessary mean that they are effective. Of those surveyed who were hit by ransomware in the last year, 64% said they had more cybersecurity budget than they need, and 24% said they had the right amount of budget. Many of these organization also said they had more headcount or the right amount of headcount (65% and 23%, respectively. This reveals that despite having ample resources—both personnel and technology—organizations will not achieve a high return on investment without a combination of the right technology and expertise to use the technology effectively.
Cyber insurance drives changes to cyber defenses

Thankfully, organizations do not have the shoulder the burden of ransomware costs all on their own. The survey found that four in five mid-sized organizations had insurance against ransomware attacks. However, 34% said there were exclusions/exceptions in their polices. Organizations that had been previous hit by ransomware attacks in the past were much more likely to have cyber insurance coverage against ransomware. However, many respondents indicated that securing coverage has changed in the past year, or gotten more difficult to obtain:
- 54% said the level of cybersecurity they need to qualify is now higher
- 47% said policies are now more complex
- 40% said fewer companies offer cyber insurance
- 37% said the process takes longer
- 34% said it is more expensive
As a result, 97% of organizations that have cyber insurance have made changes to their cyber defense to improve their cyber insurance position. 64% have implemented new technologies/services, 56% have increased staff training/education activities, and 52% have changed processes/behaviors.
Conclusion
The survey has revealed that ransomware continues to be an imminent threat for organizations of all sizes across industries. For many, choosing an experienced partner with expertise in cybersecurity not only improve their chances of getting approved for the right amount of cyber insurance coverage, but can ensure that they see an higher return on investment and improved ability to prevent and mitigate attacks in the future.
Does Your Mid-Market Firm Have the Right Talent to Maximize Its Data Tech Investments?
Does Your Mid-Market Firm Have the Right Talent to Maximize Its Data Tech Investments?
Investing in digital transformation technologies can be a waste of money if your company forgets one important point. That point is, no matter how cutting edge the tech or tool may be, people are needed with specific technical expertise in order to derive true business value from these investments.
Unlike large enterprises, mid-market companies often try to find this expertise in their IT manager, hoping a jack-of-all-trades approach will take care of it. This is an unfortunate mistake, since it would require the IT manager to have unusual command over a long laundry list of duties, from data integration, ingestion, and preparation to data security, regulatory compliance, data science, and building pipelines of data ready for executive reporting from multiple cloud and on-premises environments. This is not just a tall order for a mid-market IT manager to pull off, but likely an impossible one.

At the same time, it’s unreasonable to expect that most mid-market firms can hire an entire division of data experts—who each need to be highly compensated—in order to achieve the organization’s digital transformation goals. Even if a mid-market player could afford it—which is unlikely to make economic sense—these talent resources are scarce and in high demand.
If you’re still wondering whether your IT manager’s skill set, leveraged by your in-house IT technicians, can properly run the gamut required to achieve value from your data technology investments, consider that the person in this position would need the ability to master a wide range of skill sets, from cloud architecture, database engineering, and master data management to data quality, data profiling, and data cleansing. More specifically, your IT manager would need to take on five additional specialized roles for technical talent that are critical for achieving value from data technology investments.
These roles are:
Chief Data Officer/Chief Digital Officer
A chief data officer (CDO) is focused on—you got it—data. Most mid-market companies understandably don’t have a CDO, which means they don’t have anyone who assures regulatory compliance for data handling while managing and exploiting information assets, reducing uncertainty and risk, and applying data and analytics to drive cost optimization and revenue objectives. For IT managers to fulfill a CDO role, they’d have to be equipped to bring a global perspective to company data, help their organization gain competitive advantage over peers, and manage data and analytics. They’d also need the ability to secure data, transform it into valuable business information, lead digital transformation initiatives, and use data for growth and operational efficiency.
Cloud Engineer
The primary job of a cloud engineer is to keep cloud data centers operational and secure for ecosystem users to be able to store and access their data. Cloud engineers are experts in minimizing downtime, managing access to data, managing compute and storage, and setting up cloud architectures for clients, tenants, and containers. They also monitor data center hardware, servers, networks, and communications systems for operational continuity and efficiency.
Data Security Expert
Mid-market firms also need a way to channel the talents of a data security expert, CISO, or cybersecurity director to ensure cyber-security for the company’s data. Data security experts must keep current on emerging threats while executing data security strategies to fend off and remediate attacks. This involves a wide range of duties, including working closely with the IT team to run the company’s Security Operations Center (SOC), constantly monitoring servers, networks, and workstations for security threats, and staying up to date on the changing compliance laws and regulations for the business, to name a few. While larger IT teams have bandwidth to fill cybersecurity needs inhouse, many midmarket IT teams do not have capacity for the 24/7/365 monitoring and security edits needed to thwart attacks, let alone bandwidth for executing on mitigation and response strategies needed to overcome them.
Data Engineer
A data engineer’s primary job is to prepare data for analysis or operational uses, which involves integrating data from different sources, as well as implementing and executing data profiling, cleansing, transforming, and normalizing data. Data engineers also work with data in motion and use master data management to ensure data consistency across an organization. Finally, a data engineer is your go-to technical resource for database construction and management, helping to optimize the company’s data ecosystem.
Data Scientist
It should be clear now why a mid-market IT manager should not be expected to take on these additional professional roles, but in case there’s any doubt, keep in mind that a data scientist is also needed. Data scientists develop algorithms and leverage deep learning models to analyze data with artificial intelligence and machine learning. The data scientist creates the “brain” of the data analytics solution to position it for providing accurate answers based on business information. Data scientists also mine data to find opportunities for business growth and efficiency. Ideally, the data scientist uses tools that enable non-technical business users to query data sets without having to write SQL or other code.
Master of One
If you’ve correctly determined that your mid-market IT department does not have enough time to absorb these data roles into their regular duties of keeping your company systems stable and responding to help desk tickets from your team, don’t despair. There’s a viable solution for mid-market businesses with this dilemma: they can partner with data experts who provide a side-by-side model coupling technology with talent. This allows the mid-market to efficiently compete, leveraging the necessary skillsets to achieve digital transformation success.
What does successful mid-market digital transformation require? The key is to have a cloud-based data center, a cloud native data management platform, and cloud native analytics, thus shifting the burden of procuring and maintaining the infrastructure to a third-party vendor in the data industry. Instead of attempting to reinvent the wheel in house, mid-market players should ensure they’re partnered with the right infrastructure to maximize the data-center capabilities, and data storage and management, for effective digital transformation.
Mid-market firms can gain the benefits of working with a wide range of experts including cloud engineers, data engineers, security experts, data scientists, and other highly skilled technical resources if they establish a partnership with a data platform company. By opting for this type of side-by-side expert help, the mid-market can achieve true business value—without needing to hire an entire data team.
The Cost of Skimping on Security in 2022
From 2020 to 2021, the number of ransomware attacks on organizations increased by 78% and more than 10% of those attacks resulted in ransoms of $1 million or higher. According to the Sophos State of Ransomware 2022 report, ransomware attacks take an average of one month to fully recover from and frequently result in downtime and loss of revenue, the impact of which leads to an average recovery cost of $1.4 million. That’s about 640 vacations to Disney World. The cost of skimping on security is great.
While you could take your entire team to Disney World for a week, possibly even a few times over, a better idea might be to invest in preventing a security breach in the first place. Be it ransomware, a phishing attack, or an insider threat, proactive threat and risk prevention takes dedicated time, well-trained people, and cutting-edge technology, so it is no surprise that it can be confusing and costly. As we’ve already seen, it can be even more costly to ignore those risks.
Keeping Up with Technology
It took 2 million years for humans to progress from the first tools to discovering fire, yet it only took 130 years to go from the telegraph to the internet and another 33 years to get to the iPhone. Technology now changes at a blistering pace and, alongside that thrives the unfortunately fruitful business of cybercrime. One of the most critical factors in combating this is having, understanding, and fully utilizing the latest technology. Based on Gartner’s 2022 report of Top Strategic Trends, some of the newest technologies that will impact the cybersecurity field include:
- Cybersecurity Mesh: A scalable, integrated architecture that enables security tools to work cooperatively throughout an environment
- Autonomic Systems: Self-managing systems that take in information from the network to modify algorithms without manual updates, allowing for rapid changes and scalability
Source: Gartner
Partnering with the Experts

Whether you are intimately familiar with the concepts presented here or they sound like something from the USS Enterprise, partnering with experts is what will give you an advantage over bad actors and cyber criminals. Admittedly, most organizations struggle to keep up with regular patching, let alone investing the time and resources into implementing these types of technology. While cybersecurity and understanding cyber risk are likely not your area of expertise, working with a trusted partner can ensure that your online business and IT landscape are as secure as technology and expertise allow. Having security that stands up to the worst of ransomware, hackers, and more is a must.
The criminals don’t take a break, so your security monitoring can’t either, which is why it is critical to have both the technology to meet the needs of today’s risks as well as the people to understand, implement, and manage that technology to its fullest potential. Aunalytics has you covered. With expert toolsets and talent, your business can depend on us to have highly trained professionals and the newest technology and information to protect your business in the ongoing threat landscape.
Bridging the Mid-Market Talent Gap for Digital Transformation
Bridging the Mid-Market Talent Gap for Digital Transformation
To achieve business value from data technology investments, mid-market companies need the right technical expertise and talent. Yet many mid-market firms push this onto their IT manager, assuming that since it is technology related, IT has it. This is a mistake because most IT departments do not have time for data analytics. They are busy full time keeping company systems stable and secure, and providing support to your team members. This by necessity results in IT deprioritizing data queries over crucial cybersecurity attack prevention. Business analysts and executives get frustrated waiting for data query results, and the data is stale or the business opportunity has passed by the time query results are in.

But even if your IT team had time for it, it still is a mistake to rely on traditional technology administrators for data analytics success. This is unless your IT department has expertise across a wide range of skill sets, from cloud architecture, database engineering, master data management, data quality, data profiling, and data cleansing. What’s more, your IT manager would need to have command over data integration, data ingestion, data preparation, data security, regulatory compliance, data science, and building pipelines of data ready for executive reporting from multiple cloud and on premises environments.
When you read this laundry list of needs, it becomes clear that most mid-market IT departments lack the specialized experts needed to derive business value from their data. Unlike larger enterprises that have the resources to hire skilled staff for these roles, the mid midsize organization requires another option that provides access to the right tools, resources, and support. One that integrates, enriches and is trained in utilizing AI, machine learning, and predictive analytics to achieve more useful results.

To read more, please fill out the form below:
Learn More
Don’t Let Your Sensitive Data Go Unprotected
Every business has sensitive data that should not be shared with the world at large. Credit card information, personal details, company records—all of this data can be exposed or stolen and ransomed via a single bad actor.
Is Your Data Safe?
Everyone from banks and credit unions to government agencies and utility companies need one basic thing that can stop bad actors: good data security. With hackers and ransomware encroaching on your network, it’s more important than ever before that you have proactive data protection in place.
Good data security includes 24/7/365 monitoring of your network, constant threat and vulnerability scanning, a functioning Security Operations Center (SOC) and more. The problem? It’s hard to find talent to maintain a functional SOC, and when you do find talent your mid-market business may not be able to compete with offers from large enterprises.
While finding, paying, and retaining high quality talent is hard, partnering is not. A side-by-side approach with a knowledgeable partner allows you to actively react to the ever-changing digital landscape—not after your company’s security has been left behind and open for bad actors.
How Can You Protect Your Data?
Many security tools are made for experts—security engineers, network engineers, and others with specific technical expertise. Because the security landscape keeps changing, as bad actors evolve techniques and new threats are constantly emerging, security requires full time dedication to researching and staying up to date with threats, new prevention measures and remediation best practices. Most IT departments do not have time for the research and adaption that security requires. If you don’t have a team that can constantly update your security to provide your company with the best security possible, your security posture will begin to sag. A sagging posture isn’t good for any industry or company—and it needs to be fixed immediately.
By hiring a trusted partner, you can ensure that your sensitive data is secure. Having security that stands up to the worst of ransomware, hackers, and more is a must. An SOC takes care of things for you.
If your company doesn’t have an SOC, it is falling behind. Out of date security means injury to your network becomes more and more likely, and a security event can cause you to lose clients and prospects, large sums of money, and even tarnish your company’s reputation.
Partnering Up
You should already have an internal IT team. Aunalytics’ SOC isn’t meant to replace your IT team, but to supplement and support your team’s security initiatives. An SOC can stop threats before they enter your network and cause chaos, keeping your data out of the hands of bad actors everywhere.
When you need to protect your data, Aunalytics has you covered. With expert toolsets and talent, your business can depend on us to have highly trained experts and the newest technology and information to protect your business in the ongoing threat landscape.
Bridging the Mid-Market Talent Gap for Digital Transformation
Bridging the Mid-Market Talent Gap for Digital Transformation
To achieve business value from data technology investments, mid-market companies need the right technical expertise and talent. Yet many mid-market firms push this onto their IT manager, assuming that since it is technology related, IT has it. This is a mistake because most IT departments do not have time for data analytics. They are busy full time keeping company systems stable and secure, and providing support to your team members. This by necessity results in IT deprioritizing data queries over crucial cybersecurity attack prevention. Business analysts and executives get frustrated waiting for data query results, and the data is stale or the business opportunity has passed by the time query results are in.

But even if your IT team had time for it, it still is a mistake to rely on traditional technology administrators for data analytics success. This is unless your IT department has expertise across a wide range of skill sets, from cloud architecture, database engineering, master data management, data quality, data profiling, and data cleansing. What’s more, your IT manager would need to have command over data integration, data ingestion, data preparation, data security, regulatory compliance, data science, and building pipelines of data ready for executive reporting from multiple cloud and on premises environments.
When you read this laundry list of needs, it becomes clear that most mid-market IT departments lack the specialized experts needed to derive business value from their data. Unlike larger enterprises that have the resources to hire skilled staff for these roles, the midsize organization requires another option that provides access to the right tools, resources, and support. One that integrates, enriches and is trained in utilizing AI, machine learning, and predictive analytics to achieve more useful results.
Achieving Digital Transformation
Digital transformation has been defined by some as the integration of digital technology into all areas of a business, fundamentally changing how employees operate and deliver value to customers. Some of the challenges midsize businesses have with building an internal team to initiate this concept are employee pushback, lack of expertise to lead digitization initiatives, improper organizational structure, the absence of a digitization strategy and limited budget. As an alternative to building an internal operation, a more efficient way for mid-market businesses is to leverage the skillsets of experts by partnering with a consolidated group of experts, leveraging a side-by-side model that couples technology with talent. Look for solution providers that offer the following:

- Powerful cloud data centers paired with engineers skilled in architecting cloud-based applications and processes that better serve critical business requirements. These data centers are optimized for true multi-tenancy, built on seamlessly integrated hardware and software, offer business-driven configurability, world-class security and performant systems.
- Active Monitoring and Thoroughly Integrated Security. Monitoring and security should be pervasive across system infrastructure to defend against cyberattacks and provide remediation when required. Business customers will also expect full-time monitoring and on-demand help desk to address unexpected events. The data management platform underpinning applications should be monitored by experienced data engineers with success in building data warehouses, data lakes, and data pipes. They should also be able to integrate, cleanse, and transform data into decision-ready and analytics-ready business information.
- High ROI Business Insights that Drive Results. Data analytics investments need to provide real business value by giving actionable insights and finding opportunities within your data. With this in mind, data analytics should include access to data scientists and business analysts versed in your industry. These experts should be equipped to design AI-powered algorithms that answer the most pressing questions based on real-world business challenges.
Mid-Market Data Transformation for Enterprise-Class Results
Ensuring the right mix of hardware, software and resulting services are available to maximize the data center capabilities—and their ability to manage and protect data—is crucial to effective mid-market digital transformation. To compete and drive value, the cloud data center provider must deliver at all levels, with customizable business intelligence solutions powered by an effective data management platform that is secure and compliant. Successful mid-market digital transformation thus requires a shift of responsibilities for infrastructure procurement and maintenance to a third-party provider backed by experienced staff and best-in-class infrastructure.
When implementing a digital transformation project, your company gains from the many benefits this brings, such as a higher return on your IT investment, increased employee and customer experience, and greater business agility. This is further enhanced by leveraging experienced cloud engineers, data engineers, security experts, data scientists, and other highly skilled technical resources—achieving true business value from the investment. And by partnering with experts, your company’s time, resources, and innovation can be focused on its core competencies.
See Yourself in Cyber—How Individuals Can Reduce Security Risk
It seems like just yesterday our biggest security risk was a ‘long lost relative’ claiming we had millions of dollars waiting for us if only we would send them a little money up front. The world and technology have come a long way since then, and not always for the better. Now we are inundated with spam in the form of calls, texts, emails, and every other form of communication in existence—all alongside our actual conversations. Your grandma might message you on Facebook to ask for your help and it turns into requiring a trip to Walmart to buy $500 in Apple gift cards. Your CEO might text you with an urgent request when they’ve never texted you before. With this constant barrage of threats that continue to get more and more believable, is it even possible to be safe online? It most certainly is, but it requires vigilance and a keen, informed eye.

October is Cybersecurity Awareness Month in the US and this year’s theme is ‘See Yourself in Cyber’. Whether you’re the head of IT, a bank teller, a homemaker, or anything in between, you’re at risk of a cybersecurity attack. However, the industries experiencing the highest number of incidents are finance, healthcare, and public administration. As scammers, hackers, and generally ‘bad actors’ hone their craft, we also need to sharpen our detective skills. It’s an unfortunate truth, but we need to learn how to spot the red flags because it’s expected that, by 2025, there will be an average of 10 devices per person connected to the internet globally. All of which become a playground for cybercriminals if the devices aren’t well guarded by technology—and you.
Types of Threats
There are as many reasons bad actors attack as there are ways they do it. Understanding the most common methods will help you better avoid them in the wild. Here are some of the most widespread attacks you might see:
- Phishing: When a bad actor sends an email that appears to be from a reputable source or someone you are likely to trust in the hopes that you will open an infected attachment or follow a malicious link. This could allow them access to your system or persuade you to divulge personal information, such as passwords or credit card information.
- Spear Phishing: When a bad actor sends a phishing attack specifically targeting you. Typically, it will include information they’ve learned about you from social media or other online public forums.
- Smishing: This is phishing in the form of a text message.
- Vishing: This is phishing in the form of a phone call.
Spotting the Red Flags
For these types of threats, you’ll need to be able to identify something out of place to make you pause before taking any harmful actions. However, this is where vigilance is critical because these red flags are becoming increasingly more difficult to spot. Below you will find guidance on where you are most likely to spot a threat:
- Email is the most likely path a scammer will take. When identified separately, these signs may not seem concerning, but when combined, they are a sure sign of a phishing attack.
- Does the subject line or content of the email seem alarming or urgent?
- Is the email from someone unexpected or unknown?
- Is the ‘reply-to’ address different from the ‘from’ address?
- Did the email come in at an unusual time or day, such as in the middle of the night or on a weekend?
- Are there grammar or spelling mistakes?
- Does the wording seem unnatural?
- Are there unexpected or suspicious links or attachments?
- Are they offering you money or gift cards in exchange for an action?
- Is the email unexpected or out of place?
- Text messages may come in a different format, but they can still open you to the same security risks. Many of the red flags above still apply, but these are the most common examples in smishing.
- Is the sender claiming to be an executive at your company with an urgent need?
- If you know the sender, is the text from the number you have for them?
- Are you being asked personal information?
- Are you being asked to follow a link?
- Phone call scams commonly prey on the elderly and are more common outside of the workplace. Common signs to look for in vishing are:
- Is the call unexpected?
- Does the caller request access to your device to solve an issue?
- Does the caller threaten legal action or claim to be from a governmental body such as the IRS?
- Does the caller claim you have won money or a prize?
- Does the caller request payment in the form of gift cards or money orders?
Protecting Yourself
This feels like a lot of effort; what’s really the worst that can happen if you fall for one of these scams? If you click on a malicious link or download an infected attachment, you leave the door wide open for a hacker to access not only your device, but your entire network of devices and data. If they are able to access your personal information, they could potentially access your bank account, credit card information, or other private accounts. Shockingly, 88% of data breaches are caused by employee mistakes. Here are some steps you can take to ensure you aren’t part of that 88%:
- If an email comes from someone you work with, but you are noticing red flags, especially links or attachments, contact the person directly to verify they actually sent it.
- If there are links in the email, hover over them to ensure they match what is being displayed.
- Ensure links point to a trustworthy site. For example, you might receive an email from Microsoft asking you to reset your Outlook password, but when you hover over the link, it shows http://www.microsoftt.com/. Notice the misspelling in Microsoft.
- If you are unsure of a link, navigate to the website through your browser rather than clicking the link.
- If you receive an attachment that you didn’t expect, such as a financial statement when you don’t work in finance or a UPS shipping confirmation when you didn’t order anything, don’t open it until you can confirm its validity.
- Always remember, it is truly better safe than sorry when it comes to suspicious links or attachments.
This is just a small window into an ever-changing landscape of security threats. It might feel impossible to keep up as threats evolve, but there are ways to stay informed and vigilant for both you and your company. Through its Secure Managed Services Solution, Aunalytics provides the tools and talent you need to stay protect from outside threats, include a streamlined training platform to ensure you and your team can stay up-to-date with current threats and reduce security risk. When you are able to ‘See Yourself in Cyber’, you become critical in fighting against bad actors and the cyber threats they pose.
Aunalytics Security Operations Manager Rob Bradford to Deliver a Talk on the Cost of Skimping on Security in 2022 at BankTech Conference, Attended by Illinois, Indiana, Michigan, and Ohio Bankers
Leading Data Management and Analytics Company Will Feature Its Managed Services Solutions for Improving Operational Efficiencies and Reducing the Risks Associated with Cyber Attacks at Two Banking Events in October
South Bend, IN (September 29, 2022) - Aunalytics, a leading data management and analytics company delivering Insights-as-a-Service for mid-market businesses, announced today that Rob Bradford, Security Operations Manager for Aunalytics, will discuss The Cost of Skimping on Security in 2022 at the BankTech Conference on October 6. The company will also showcase its managed services, enterprise cloud, and data cleansing portfolio at the conference, in addition to the Indiana Bankers Association’s Security & Technology Conference, October 4-6.
Cyber-attacks are an increasing concern, especially for financial services firms which may experience up to 300 times more cyber attacks per year than other firms. Cyber criminals continue to double down efforts to breach financial data, compromise accounts, and profit from this industry with increasingly sophisticated attacks and campaigns. It is more critical than ever that banks work with the right IT services providers who have the security expertise, up-to-date knowledge of industry developments, and comprehensive tools to maintain a strong defense against cyber threats.
Aunalytics provides IT and security expertise to mid-market businesses in the areas of financial services, healthcare, manufacturing, professional services, and cities and local government. The company’s Secure Managed Services offering combines mission critical IT services leveraging zero-trust, end-to-end security to ensure data is protected regardless of a user’s location. Aunalytics provides managed components that offer stability and security, and its next-generation managed services offering is powered by a data platform that provides data-driven IT answers and embedded security that focuses on people and access.
The full suite of managed IT and integrated security services empowers businesses with a complete, all-encompassing approach that includes 24/7/365 monitoring and management, a synchronized network security platform, workstation and server patching, internet protection, email filtering and security, Office 365 management and security, multi-factor authentication, data and device encryption management, and security awareness training.
The company delivers advanced security for defending against modern threats through a team of engineers and analysts with expert skills and toolsets and, in regulated industries, Aunalytics provides the additional technology and controls required to manage risk. Its team of experts is dedicated to analyzing ever-changing rules and regulations and helping users to create processes and policies for data protection and meet compliance requirements within those industries that are regulated.
Aunalytics’ Enterprise Cloud offering is comprised of infrastructure solutions that provide a highly redundant and scalable platform for hosting servers, data, analytics and applications at any performance level. With the Aunalytics® Cloud Storage and Compute solution, users are assured the highest levels of security, accessibility, expertise, scalability, and savings. Aunalytics’ data centers, located in Northern Indiana and Southwest Michigan, meet the most rigorous compliance standards.
“Cyber security continues to be an important concern for banks and other financial institutions while cyber criminals are increasingly adept at executing attack campaigns,” said Steve Burdick, Vice President Sales, Cloud & Managed Services Aunalytics. “Working with a managed services provider who has the expertise to help with such things as vulnerability testing, proactive threat hunting, and ongoing monitoring helps reduce the burden on internal IT resources. Aunalytics’ full suite of managed IT and integrated security services solutions provides the tools and people resources mid-market banks need to adequately improve their security postures and maintain the highest levels of IT security to thwart cyber-attacks and reduce risk.”
Tweet this: .@Aunalytics Security Operations Manager Rob Bradford to Deliver a Talk on The Cost of Skimping on Security in 2022 at BankTech Conference, Attended by Illinois, Indiana, Michigan, and Ohio Bankers #Informationtechnology #Managedservices #Enterprisecloud #Datacleansing #Dataplatform #Dataintegration #Dataaccuracy #Digitaltransformation #ITsecurity #Securitytechnology #Banking #Midmarketbanks #Creditunions
About Aunalytics
Aunalytics is a leading data management and analytics company delivering Insights-as-a-Service for mid-sized businesses and enterprises. Selected for the prestigious Inc. 5000 list for two consecutive years as one of the nation’s fastest growing companies, Aunalytics offers managed IT services and managed analytics services, private cloud services, and a private cloud-native data platform for data management and analytics. The platform is built for universal data access, advanced analytics and AI – unifying distributed data silos into a single source of truth for highly accurate, actionable business information. Its DaybreakTM industry intelligent data mart combined with the power of the Aunalytics data platform provides industry-specific data models with built-in queries and AI for accurate mission-critical insights. To solve the talent gap that so many mid-sized businesses and enterprises located in secondary markets face, Aunalytics’ side-by-side digital transformation model provides the technical talent needed for data management and analytics success in addition to its innovative technologies and tools. To learn more contact us at +1 855-799-DATA or visit Aunalytics at https://www.aunalytics.com or on Twitter and LinkedIn.
PR Contact
Denise Nelson
The Ventana Group for Aunalytics
(925) 858-5198
dnelson@theventanagroup.com
5th Annual BankTech Conference
5th Annual BankTech Conference
Chicago Marriott Southwest, Burr Ridge, IL
Aunalytics to Present at the 5th Annual BankTech Conference and Participate at the Innovators' Showcase
Aunalytics is proud to participate in the 2022 BankTech Conference on October 6, 2022 in Burr Ridge, IL. Rob Bradford, Security Operations Manager at Aunalytics, will be presenting the talk, “The Cost of Skimping on Security in 2022” at 10:15am central time. Representatives from Aunalytics will also be showcasing our Secure Managed Services IT offering as well as our Advanced Security solution during the Innovators’ Showcase.

2022 Indiana Bankers Association Security & Tech Conference
2022 Indiana Bankers Association Security & Tech Conference
Renaissance Indianapolis North Hotel, Carmel, IN
Aunalytics is Proud to Attend the 2022 IBA Security & Technology Conference
Aunalytics is proud to participate in the 2022 Indiana Bankers Association Security & Technology Conference from October 4-6, 2022 in Carmel, IN. Representatives from Aunalytics will be showcasing our Secure Managed Services IT offering as well as our Advanced Security solution.