What Mid-Market Companies Need for Data-Driven Success and How to Get It
What Mid-Market Companies Need for Data-Driven Success and How to Get It
Using your data as an asset to drive competitive business growth and achieve cost cutting operational efficiencies is imperative for a company to compete, survive, and thrive. Increasingly, data and analytics have become a primary driver of business strategy and the potential of data-driven business strategies is greater today than ever.
Proactive Security Measures Prevent and Mitigate Cybersecurity Attacks
Does your enterprise’s security stand up to today’s threats? Cyberattacks have increased to higher than ever levels and bad actors are attacking with increasing sophistication. It has been reported that ransomware attacks increased over 90% in 2021, with demands for payment skyrocketing into tens of millions of dollars. In addition, with remote work more prevalent than ever, most businesses now hold some form of sensitive data in the cloud and workers access company data from remote locations. Securing many different locations can be a challenge. Because of these factors, your security infrastructure in place today may still have gaps. Fortunately, proactive security prevents cyberattacks. Therefore, a security operations center (SOC) is the most essential element of modern security. But SOCs are expensive, complicated, and far beyond the reach of most small to midsize enterprises. Plus, security expertise is not easy to recruit and retain internally.
At Aunalytics, we constantly enhance our knowledge to keep up with progressively complex attacks. Aunalytics provides proactive measures for prevention, detection & response by identifying vulnerabilities and threats through a single, unified service. Our data platform examines intel from different sources with the goal of providing insight to your organization needed to best protect your technology environment. Pairing our data platform with the top cybersecurity solutions in the industry gives our clients peace of mind with our complete, holistic approach.
Watch the video below to learn more about Aunalytics Security solutions:
Since proactive security prevents cyberattacks, businesses need access to expert skills in cloud security and data security, which is not standard in mid-market IT departments. That is why our Aunalytics Advanced Security solution includes everything mid-market businesses need to manage risk, including:
- Comprehensive security operations solutions
- Customized security alerting and vulnerability prioritization
- Proprietary, cloud-based security platform
- Continuous vulnerability scanning
- Predictable, consistent pricing
- Threat intelligence and other security data
- Dedicated security engineers X 24×7 detection and response
When your business requires the highest level of security, Aunalytics has you covered. Our security experts stay up to date, so you can focus on your business.
Aunalytics Managed IT Services Safeguard Logan County Ohio Against Disruptive Weather, Cyber, and Pandemic Events
Aunalytics Managed IT Services Safeguard Logan County Ohio Against Disruptive Weather, Cyber, and Pandemic Events

Fill out the form below to receive an email with a link to the case study.
Aunalytics is a data platform company. We deliver insights as a service to answer your most important IT and business questions.
Featured Content
Nothing found.
Aunalytics Managed IT Services Safeguard Logan County Ohio Against Disruptive Weather, Cyber, and Pandemic Events - PDF
Aunalytics Managed IT Services Safeguard Logan County Ohio Against Disruptive Weather, Cyber, and Pandemic Events
Related Content
Nothing found.
Ransomware Attacks Now Target Community Businesses
If you think that your business will not be a target for ransomware attackers, think again. This is no longer a problem only for large enterprises—now, ransomware attacks target community businesses as well.
The Battle Creek, Michigan community woke up to a May Day attack that forced its Kellogg Community College (KCC) to close all operations. In the middle of preparations for final exams, all five campuses serving approximately 6900 students closed and all operations came to a screaming halt.
The community college posted alerts on its website and social media:
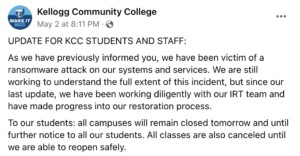
Eric Greene, the Vice President for Strategy, Relations, and Communications at KCC said: “We are still working to understand the full extent of this incident, but as soon as we became aware of it, we immediately assembled a multi-disciplinary team and engaged independent legal counsel and external forensic experts.”
Greene continued, “KCC had backups in place, and we are working systematically with our IT experts to restore our operations.” But even though KCC had backups, “As a precautionary measure, all campuses have been disconnected and our systems will remain offline until they are deemed secure by our IT experts. As a result, our students and staff might experience delays accessing our services, including campus emails, online classes, and resources,” Greene said.
Back-ups alone are not sufficient to prevent business disruption when a ransomware attack hits. Preventing the attack, rather than having to respond to it, is key. KCC remained closed for three days while IT scrambled. All computer access to university systems had to be shut down in an attempt to stop further damage. The response and mitigation included a forced password reset for all students, faculty and staff, and adding multi-factor authentication (MFA) for all users.
Enable Multi-factor Authentication
MFA is an important security measure when people access systems remotely. It provides an extra level of verification to make sure that the user attempting to access the system is really an authorized user and not a bad actor trying to get in. Modern business regularly includes employees logging in from home, travel and mobile devices to access data and systems from their organization. As such, the old firewall security perimeter around your place of business does not protect you. Modern security requires focus on users and access. MFA is something that is easy to add to your security stack. The protection benefit from MFA far outweighs the resource cost of installing and using the technology. Really, there is no excuse for not having MFA in today’s threat landscape. It is standard.
So if you do nothing else this year to improve your security posture, add MFA. But considering that community businesses are becoming targets for cybercrimes, unless you can afford a complete shut-down of your business, it is becoming a must to have modern security technologies (including robust monitoring so that you are equipped to prevent attacks and are better positioned to respond and mitigate), in addition to back-up and disaster recovery plans.
Shift Applications to the Cloud
Mid-market businesses are shifting security and data center responsibilities from on premise servers and security maintained by their IT department, to partnering with cloud experts who run data centers, keeping client systems stable and secure as their full time business. The trend with line of business applications used by your team for daily operations is cloud. As more and more community businesses use cloud based apps for functions like accounting, customer portals, ERP, CRM and HR, having cloud experts with the tools and the skills to be able to secure your organization’s data (from multiple sources) for safe use by remote users makes more sense than trying to build a security fortress yourself at your place of business.
Partner with Experts
If cybersecurity is not your main line of business, partner with security experts unless you want cybersecurity to become your main line of business. It will consume your resources to stay current with emerging threats, protective means, 24/7/365 monitoring, best practices and constantly evolving security measures. The ever increasing sophistication and volume of attacks has shifted the answer to the “buy it or build it” question for this critical business service from the solution being your in-house IT department to the solution requiring managed security services to supplement your in-house IT team.
Don’t become the next ransomware attack headline. Community businesses can take steps to avoid ransomware attacks. An ounce of prevention, after all, is less costly than the cost of operational shut-down, PR scramble, customer service disruption, brand reputation tarnishment, and emergency security consultant fees paid when you are in the middle of an attack that succeeded.
2022 Grand Rapids IT Symposium
Grand Rapids IT Symposium
DeVos Place, Grand Rapids, MI
Aunalytics to attend the 2022 Grand Rapids IT Symposium
Aunalytics is excited to showcase its Secure Managed Services and Advanced Security offerings at the 2022 Grand Rapids IT Symposium. The Aunalytics service stack combines mission critical IT services leveraging zero trust end-to-end security to ensure people and data are protected regardless of location.

MMTA 2022 Basic Institute
2022 Basic Institute
Michigan Municipal Treasurers Association
Mt. Pleasant, MI
Steve Burdick presenting "Mobile Offices & Working Remotely" at the MMTA 2022 Basic Institute
Steve Burdick, Vice President of Sales – Cloud, will be presenting “Mobile Offices & Working Remotely” at the 2022 Basic Institute event presented by the Michigan Municipal Treasurers Association. Steve will be giving tips on how organizations can keep their mobile workforce both comfortable and secure.

Managed IT Services and Data Recovery Offerings from Aunalytics Solve Emergency IT Challenges for EMI
 Over the past several years, information technology has taken center stage at Ohio-based landscaping company Environmental Management Inc. (EMI). Established more than two decades ago, EMI has grown to be one of the largest landscape companies in Central Ohio. Serving major business and governmental customers throughout the region, EMI continues to grow, thereby increasing demand for managed IT services in multiple business areas.
Over the past several years, information technology has taken center stage at Ohio-based landscaping company Environmental Management Inc. (EMI). Established more than two decades ago, EMI has grown to be one of the largest landscape companies in Central Ohio. Serving major business and governmental customers throughout the region, EMI continues to grow, thereby increasing demand for managed IT services in multiple business areas.
Managing business-critical IT environments is a time-consuming process that many times can require specialists with the experience to deliver the highest performing infrastructure possible. EMI has seen this first-hand over the past several years as the company has had to recover from destroyed network infrastructure caused by a catastrophic lightning strike, a disruptive cyberattack involving ransomware with the encryption of important company information, and the need to reconfigure its computing endpoints quickly because of the occurrence of Covid-19 to accommodate “work from home” environments for its team.
Aunalytics provides a broad range of managed IT solutions, including network, server management, and PC management, as well as Office 365, data recovery and business continuity support. EMI employed several services which have helped to positively transform the company’s operations.
The side-by-side support model employed by Aunalytics has been an especially impactful benefit of this partnership. “While there are many important services provided, perhaps the most widely used and important for EMI is the 24×7 help desk which is essentially an IT department on demand,” said Tom Kiefer, CFO for EMI. “Whether it’s an employee who accidentally deleted a file or a catastrophic lightning strike, the team behind the Aunalytics Ohio help desk has been insightful and fast to act, allowing our employees to remain online and productive.”
Read the full case study to see how EMI further benefitted from the managed IT and data recovery services provided by Aunalytics Ohio.
Financial institutions are frequently targeted in cyberattacks—here’s how to protect your bank or credit union
 Financial institutions consistently have been the most cyberattacked industry for the past decade. It is no surprise, given that banking enterprises hold large volumes of sensitive data about people, companies, and governments, and their transactional business revolves around massive volumes of money transfer. Hackers will continue to strike with increasing sophistication since the data held by financial institutions is of high value with the potential for extremely lucrative financial gains if stolen. For example, the Europe-based Carbanak and Cobalt malware campaigns targeted more than 100 financial institutions in greater than 40 countries during five years from 2013-2018, and the criminal profits yielded over a billion Euros.
Financial institutions consistently have been the most cyberattacked industry for the past decade. It is no surprise, given that banking enterprises hold large volumes of sensitive data about people, companies, and governments, and their transactional business revolves around massive volumes of money transfer. Hackers will continue to strike with increasing sophistication since the data held by financial institutions is of high value with the potential for extremely lucrative financial gains if stolen. For example, the Europe-based Carbanak and Cobalt malware campaigns targeted more than 100 financial institutions in greater than 40 countries during five years from 2013-2018, and the criminal profits yielded over a billion Euros.
Attacks are increasingly sophisticated and cyber criminals continue to invest in new and complex criminal strategies and campaigns. Hackers in banking often take advantage of the interdependencies of financial institutions to service products such as credit cards and mortgages for other banks. From one bank breach, the cyber cartels jump to the partnered financial institution to steal its data as well.
In some types of cyberattacks, criminals make slight changes to data, which may not be immediately detectable. Because nothing is stolen at the time, users may not recognize the attack. However, once the criminals gain access to this data, they can manipulate algorithms in the system for their own financial gain. Timestamp manipulation is a newer strategy, whereby criminals have found that they are more likely to evade detection if they manipulate time for an otherwise valid transaction. Changing timestamps can alter the value of capital and trades. Because the parties to the transaction appear to be legitimate, this type of fraud is harder to detect.
Other criminals outright steal data for financial gain by selling it, hold data hostage for ransom profit, or pilfer intellectual property such as an organization’s competitive strategy and business plans to sell to interested parties. But the main goal in banking cyber-criminal activity is direct profit from a modern-day bank heist—stealing money from the bank.
Despite the increasing complexity of cyberattacks against financial institutions, there are some tools and best practices that banks and credit unions can use to protect themselves from these threats:
- Continuously update security technology and protocols as threats evolve and adapt with the help of a dedicated full-time security team.
- Employ 24/7/365 monitoring with remote remediation to quickly stop attacks in their tracks
- Monitor endpoint devices to stop attacks before they hit networks.
- Monitor cloud security including application use across the financial institution.
- Monitor email and Office 365 using tools specially designed to thwart attacks on these platforms, such as proactively recognizing and removing phishing scams.
- Have a dedicated security team and SOC, or hire an expert outside managed security services firm that embeds tools, technology and 24/7/365 monitoring to serve as your SOC.
- Push frequent patches so that user devices are equipped with the latest security protections.
- Adopt deep learning or AI monitoring, mitigation and context investigation that can more quickly identify threats.
- Encrypt data so that it is not compromised even if a breach occurs.
- Use multi-factor authentication to protect against unauthorized access.
- Instruct employees and customers to only access bank data in a secure location over a non-public Internet connection.
- Train employees on cybersecurity threats quarterly.
- Develop a solid business recovery plan for when an attack occurs.
Learn more about how Aunalytics Advanced Security helps protect financial institutions, and businesses in other highly regulated industries, from cyberattacks.