Think You Know Ransomware? The Faces of Cybercrime: The Hunters and The Hunted
Ransomware attacks are not simply a nuisance—a single attack can affect thousands of computers and servers, cost companies huge sums of money, or prevent businesses from operating altogether. And it’s not just large corporations that are at risk. Governments, universities, police forces, healthcare organizations, and even small businesses are brought to their knees by cybercrime. Anyone can be a victim—it can be as simple as one person clicking on a malicious link in an email.
Once attacked, organizations are faced with a dilemma. Either pay a large ransom and hope the attacker will actually provide the key to recover their data, or try to mitigate the loss of data on their own, which can be expensive and extremely time consuming. Yet, even if an organization chooses to pay a ransom to recover data right away, they will likely still face negative consequences from the breech, including lost productivity, risk of litigation, and loss of customer trust.
Despite the magnitude of this issue, it has been very difficult for authorities to catch and prosecute cybercriminals. In fact, the problem is only getting worse as these individuals continue to succeed in making large sums of money from the comfort of their own homes—without facing any consequences.
Why are cybercriminals able to flourish, and what can we do to stop them? Part two of Sophos‘ documentary series on ransomware explores the risks of cybercrime to organizations both large and small, and examines the various factors that have led to an increase in ransomware attacks.
View the episode on Vimeo.
Are you certain your organization is fully protected? If you aren’t sure, the security experts at Aunalytics can help you determine your organization’s risk. We offer a complete suite of managed security services and maintain a highly secure cloud environment utilizing security best practices. Aunalytics partners with leading technologies in the security field, such as Sophos, to ensure that your organization always stays a step ahead of hackers and other bad actors. Don’t leave your organization vulnerable—contact Aunalytics today.
Think You Know Ransomware? The Origins of Cybercrime
How well do you know ransomware? Security hacks and ransomware attacks are constantly in the news. In fact, in June 2023, a zero-day vulnerability in Progress Software’s MOVEit Transfer managed file transfer (MFT) product affected over 130 organizations and millions of individuals. And that is only the latest in a constant stream of cybercrime.
Since the advent of the internet, hackers have been developing increasingly sophisticated attacks. But what is most concerning may be that what was once only achievable by highly-skilled hackers is now accessible to anyone. Would-be cybercriminals can easily access the tools and knowledge via the internet to mount an attack. Currently, that most often takes the shape of a ransomware attack—which makes any industry with data a target. Despite this fact, many organizations and individuals continue to remain vulnerable.

Sophos, a leading security software and hardware company, and one of Aunalytics’ technology partners, has released a three-part documentary series examining the history of cybercrime and how it affects everyone—from small businesses to local and national governments. The first episode examines origins of cybercrime and explores why many interconnected systems are susceptible to ransomware attacks. Watch it below:
View the episode on Vimeo.
Are you certain your organization is fully protected? If you aren’t sure, the security experts at Aunalytics can help you determine your organization’s risk. We offer a complete suite of managed security services and maintain a highly secure cloud environment utilizing security best practices. Aunalytics partners with leading technologies in the security field, such as Sophos, to ensure that your organization always stays a step ahead of hackers and other bad actors. Don’t leave your organization vulnerable—contact Aunalytics today.
VMUG Indianapolis UserCon 2023
VMUG Indianapolis UserCon 2023
The Westin Indianapolis, Indianapolis, IN
Aunalytics to Attend VMUG User Group Indianapolis as a Bronze Sponsor
Aunalytics is excited to attend the VMWare User Group’s 2023 UserCon – Indianapolis. Aunalytics is participating as a Bronze sponsor and our team is excited to connect with fellow IT professionals to discuss digital transformation and innovation in the technology field.

A Managed IT Services Partner Gives In-House IT Teams Much-Needed Support
Managing IT environments is a little bit like a box of chocolates—you never know what you’re going to be faced with on any given day. Regardless of the size of your business, your company still has a unique IT infrastructure that can be difficult to manage easily and efficiently. Those variabilities are where a beneficial relationship with an experienced managed IT services partner comes into play.
Partnering with a managed services provider gives you many advantages, including support and improvement for your security initiatives, increased efficiency in your everyday technology environment, and a happy partnership can lead to cost savings in the long run.

Let’s dive a little deeper into the advantages mentioned above:
- Improved security initiatives and better support – Business organizations are often targeted by bad actors due to not only the amount, but also due to the value of the data that can be gained from stealing your important information. By providing security services, an experienced partner can better protect and insulate your company from cyberthreats. Those security services could include constant vulnerability scanning, manning a Security Operations Center (SOC) when your team is too small or too spread out to do so, and even work with you on patch management.
- Increased efficiency – By reducing downtime in case of attack and bringing productivity back online as quickly as possible, a managed IT services partner helps keep your company up and running efficiently. In addition to keeping your company up and running from a security standpoint, a managed services partner can also help keep your data safe in case of disaster, system wipe, and more, allowing you to get back to doing what you do best as quickly as possible.
- Cost savings – By giving your company access to advanced cloud-based technology and a drove of experts right at their fingertips, you can reduce large capital expenditures and avoid hiring more expensive full-time employees (FTEs). Let the experts do the work for you, giving your team the ability to focus on your internal initiatives instead of attempting to defend your network while shorthanded.
Regardless of your needs, enlisting the help of a managed IT services partner can help ease the burden on your business in both the short- and long-term, allowing your team to focus on working toward the future of your company with experts at their sides, helping them every step of the way. Not only is it a burden off of your team’s shoulders, but it’s also a burden off of your shoulders. Knowing that your company is secured by both your team and a trusted managed services partner gives you the peace of mind that, no matter what happens, your company is safe from serious cyber threats.
From Backup & Disaster Recovery to Cloud Storage and Advanced Security, Aunalytics offers a wide variety of managed services products, all backed by our certified and talented technology experts. We are here to work with you through both your everyday needs and those moments when disaster strikes.
Defense Manufacturers Face Huge Risks from Malware
Manufacturers that work with the Department of Defense (DoD) are immune to attacks of any kind, right? Wrong. Like any industry, the companies that produce equipment and military systems are just as vulnerable to malware.
Malware is a blanket term used for any kind of software that is designed to cause harm to a digital environment like your office or factory spaces. It can damage devices, computer systems, and networks while bad actors ensure all business functions come to a screeching halt—frozen in place while your files are accessed, stolen, and possibly even sold. With such valuable, and often proprietary, information, defense manufacturers may be an even bigger target than others and can lead to a national security incident. What are some ways that malware can cause serious issues for defense manufacturers?
Disrupted Operations and Processes
The first issue is the most obvious—by using malware, hackers can access your network and put a halt to your internal processes.
Shutting down operations is a big deal for anyone, but when you work with the DoD, the delays and backups during equipment production and delivery of goods can lead to significant delays that impact military readiness.
Theft of Intellectual Property
In addition to being used to disrupt operations, malware can also be used to steal and encrypt or sell sensitive information connected to the development and production of equipment made for the DoD.
Bad actors can disrupt or shut down vital systems, encrypt your data, and openly steal your proprietary information in hopes you will pay them to restore it. It is exceptionally rare that a company receives all its data back after a ransomware attack and there is no way to guarantee the data wasn’t copied before being returned. Additionally, once you’ve paid the first ransom, it has become increasingly common for bad actors to charge additional ransoms before returning your data.
Due to the sensitive nature of the information, it can be used to sell competing products, sell counterfeits, and more, potentially giving an unfair advantage.
Compromised Security
You may have seen this coming. Theft of intellectual property often leads to every DoD manufacturer’s nightmare—especially where drones or other vital systems concerned—compromised security.
Since malware can be used to attack and enter the compromised security of a manufacturing company, including its networks, it allows attackers direct access to sensitive, and sometimes dangerous, equipment. You don’t want to give away your company’s ‘nuclear football’.
What now?
Thankfully you can make this an ‘if’ not a ‘when’ situation—there are ways that such attacks can be avoided and guarded against. In addition to the advanced security measures that are recommended, employee cybersecurity training must be implemented. It’s not enough to have good security—everyone with access to your company’s data must be able to recognize a bad actor when they see one.
Partnering with a Managed IT Services company that specializes in protecting against cybersecurity threats means you can focus on what you do best—helping the DoD protect our country. As one of the only FedRAMP certified companies in the Midwest, you can depend on Aunalytics to keep your sensitive data safe. Don’t settle for an out-of-the-box antivirus and nothing else. Ensure that your location and data are not only secure, but that they will remain that way—no matter what the threat landscape looks like.
How State and Local Governments Can Use Technology to Overcome Economic Challenges
How State and Local Governments Can Use Technology to Overcome Economic Challenges
At present, state and local governments are confronted with significant challenges stemming from the current state of the economy. This includes a decrease in tax revenues, sustained high inflation, and a shortage of proficient IT personnel, who are vital to their day-to-day operations. Industry experts consider technology as an effective solution to address inadequacies during challenging economic periods.

Fill out the form below to receive a link to the article.
Aunalytics is a data platform company. We deliver insights as a service to answer your most important IT and business questions.
Government Resources
Nothing found.
How State and Local Governments Can Use Technology to Overcome Economic Challenges
How State and Local Governments Can Use Technology to Overcome Economic Challenges
At present, state and local governments are confronted with significant challenges stemming from the current state of the economy. This includes a decrease in tax revenues, sustained high inflation, and a shortage of proficient IT personnel, who are vital to their day-to-day operations. Industry experts consider technology as an effective solution to address inadequacies during challenging economic periods.
Local and State Government Cyberattacks Prove that Security is a Necessity
Cyberattacks are a constant threat to organizations of all sizes. State and local governments are no different, having experienced significantly more cyberattacks than they did in previous years, and are at very high risk of bad actors slipping into their networks. To gain a better understanding of the current attack environment and track changes over time in ransomware trends, Aunalytics security partner Sophos commissioned an independent, vendor-agnostic survey of 5,600 IT professionals across multiple industries in mid-sized organizations across 31 countries. While it’s true cyber insurance has been playing a greater role in helping organizations improve their ability to recover from attacks, survey responses clearly indicate that ransomware poses a rising threat to government organizations.
Government Cyberattacks Increase From Previous Years
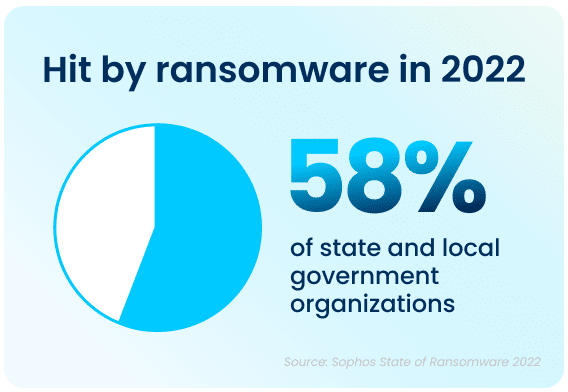
Ransomware attacks have increased significantly over the past year—58% of state and local government organizations surveyed were hit by an attack in 2021, up 70% from 2020. Bad actors are now considerably more capable of attacking organizations and executing harmful tactics at scale. The Ransomware-as-a-Service (RaaS) model is one cause of last year’s increased attacks, as the required skill level for bad actors to hamper the day-to-day operations of an organization has gone down significantly.
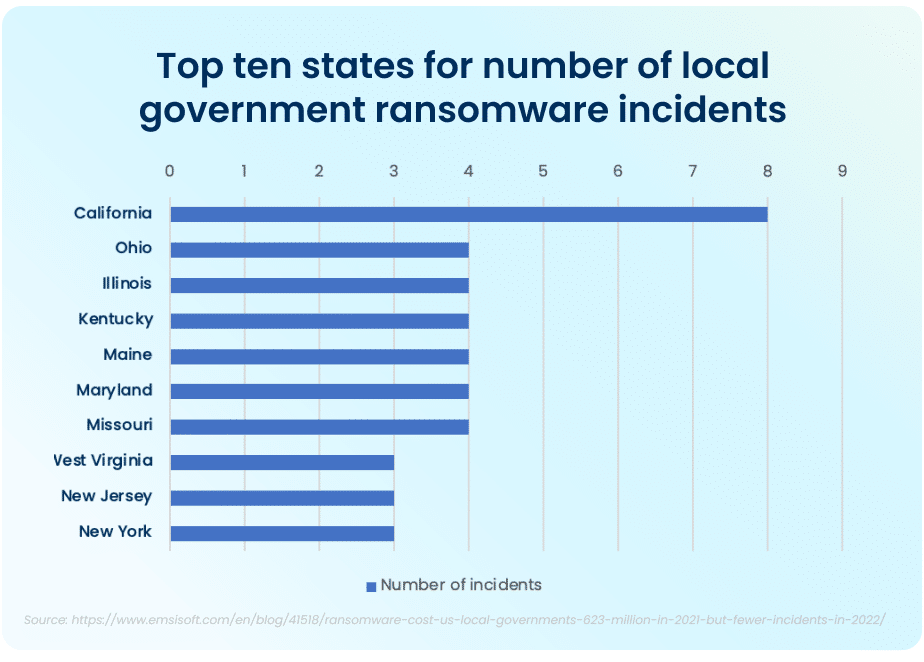
The top ten states that had to deal with the maximum amount of total ransomware attacks in the public sector in 2021 were California, who experienced the most attacks total, Ohio, Illinois, Kentucky, Maine, Maryland, and Missouri. While California took the lion’s share of attacks, with 8 major ransomware incidents, the other six states had four major incidents each.
FBI Cyber Division Survey Lists Examples of Ransomware Attacks
The Federal Bureau of Investigation (FBI) Cyber Division lists examples of several ransomware attacks that impacted state and local government organizations in their 2022 Private Industry Notification. This list contains evidence showing the impact these attacks can have on local communities.
For example, in January 2022, following a ransomware attack, a US county had to take all their systems offline and close all public locations in order to run an emergency response plan and restore all their data from backups. This action disabled all the cameras in the local county jail and deactivated automatic doors, resulting in severe safety concerns and a complete lockdown of the facility. A different county had their data—with residential and personal data—held ransom in an attack. When the ransom was not paid, all of the data was posted on the Dark Web in retaliation.
Rising Complexity of Ransomware Attacks
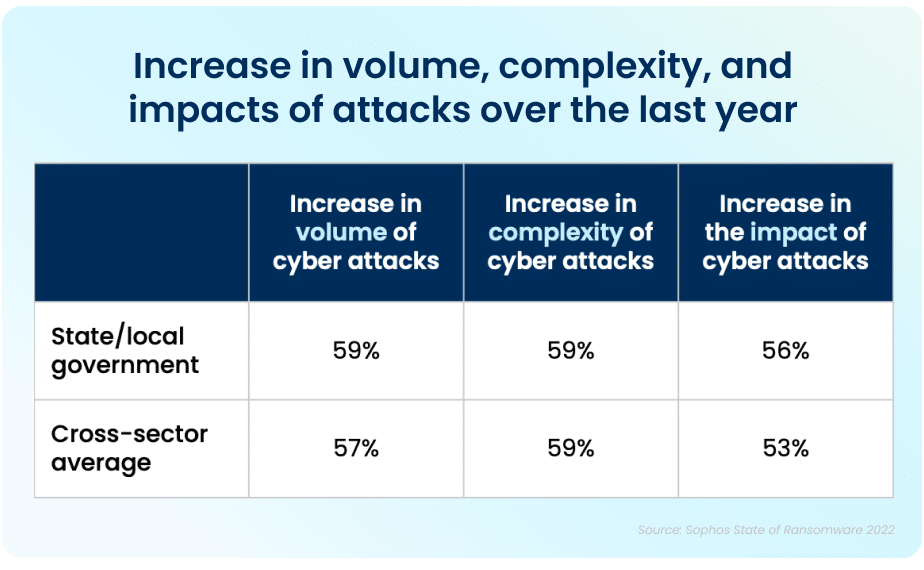
Apart from the rising prevalence of these attacks, the sheer complexity of each attack is also on an upwards trajectory. While the manufacturing and production industry reported the lowest rate of ransomware attacks, over half of all respondents reported their organization was injured by bad actors. The reality is that every organization is at high risk of cyberattack. In 2021, 59% percent of government organizations who experienced cyberattacks saw the complexity of the attacks increase, while a similar 59% saw an increase in the overall volume of cyberattacks.
Data Recovery Rates Are Improving
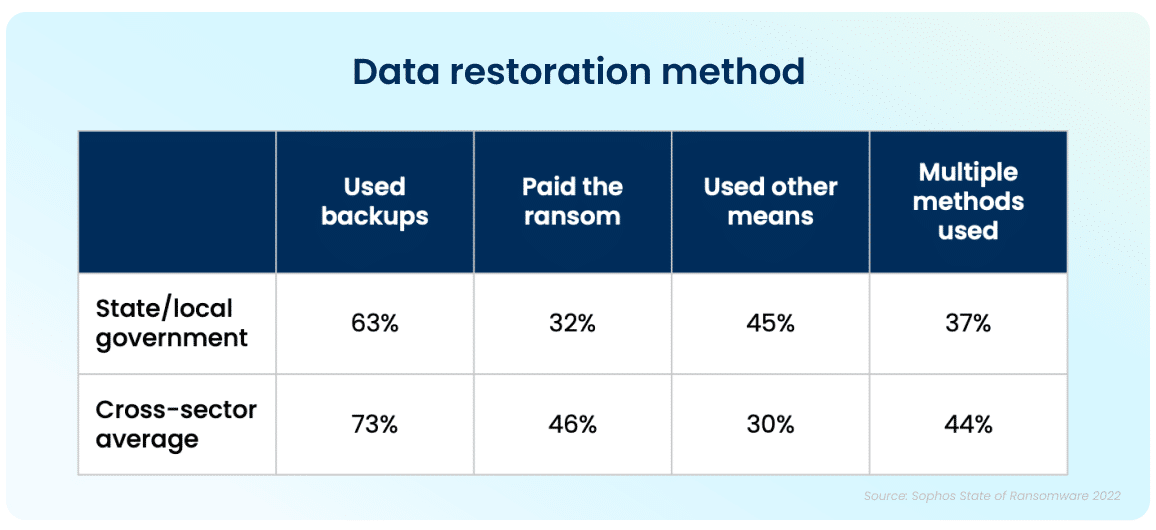
While the increase in cyberattacks paints a bleak picture, there is a silver lining to this dark cloud. Ninety-nine percent of government organizations were able to get at least some of their encrypted data back. The top method used to restore data was performed via existing backups, which were used by 63% of organizations whose data was encrypted in an attack. Unfortunately, despite the utilization of backups, 32% of the affected organizations still had to pay a ransom to ensure that more of their data was restored.
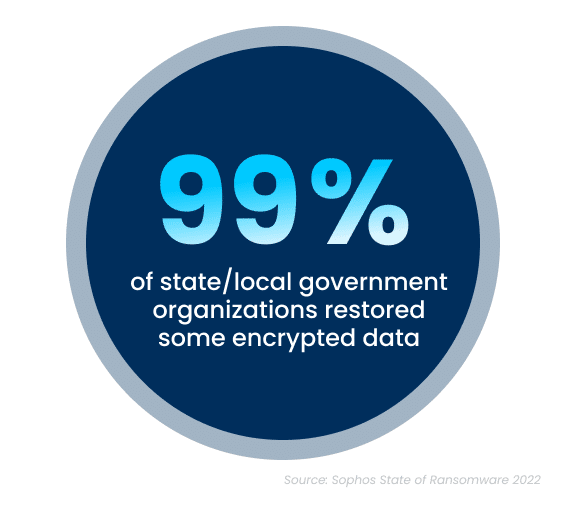
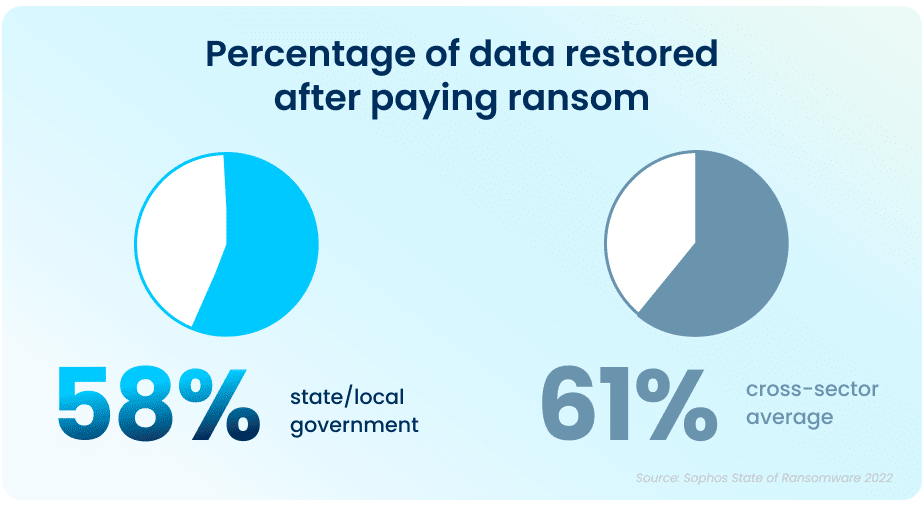
While paying a ransom typically allows organizations to get some data back, it is proving to be less effective than in years past. On average, in 2021, organizations that paid a ransom only got back 58% of their data, a considerable drop from 70% in 2020.
In April and June 2022, respectively, the states of North Carolina and Florida were the first states to prohibit state and local government organizations from paying ransoms to any bad actors. Arizona, Pennsylvania, Texas and New York are considering similar legislation. While the exact impact of this cannot be determined yet, this is expected to dissuade ransomware attacks on all organizations.
This highlights the importance of employing multiple methods to restore data—utilizing backups in particular can improve the speed of recovery and increase the amount of data that can be recovered in the event of an attack.
But It Doesn’t End There
The Sophos State of Ransomware In State and Local Government 2022 survey has revealed that ransomware continues to be an imminent threat for state and local government organizations. For many, choosing to work with an experienced partner with expertise in cybersecurity not only improves your chances of getting approved for the right amount of cyber insurance coverage, but can also ensure that companies see a higher return on investment, and improved ability to both prevent and mitigate attacks in the future. Aunalytics provides Disaster Recovery Services, which is further coupled with a comprehensive backup and archival strategy. This allows state and local government organizations like yours to remain confident so that you are prepared should you encounter a disaster event. We partner with industry leaders to replicate your critical infrastructure so you are prepared for anything.
Security Maturity Improvement is Imperative as Cyberattack Risks Remain High
Security Maturity Improvement is Imperative as Cyberattack Risks Remain High
While advancing technology offers significant benefits, it has also made it easier for those who seek to gain an advantage by exploiting others. An attack can be devastating for any business and impact it for many years to come—today’s organizations need to move toward security maturity by utilizing multiple lines of defense against cybercrime.
Fill out the form below to receive a link to the article.
Aunalytics is a data platform company. We deliver insights as a service to answer your most important IT and business questions.
Security Maturity Improvement is Imperative as Cyberattack Risks Remain High
Security Maturity Improvement is Imperative as Cyberattack Risks Remain High
While advancing technology offers significant benefits, it has also made it easier for those who seek to gain an advantage by exploiting others. An attack can be devastating for any business and impact it for many years to come—today’s organizations need to move toward security maturity by utilizing multiple lines of defense against cybercrime.